Urlbuster:一款支持爆破的可变异Web目录模糊测试工具
Urlbuster是一款功能强大的Web目录模糊测试工具,该工具可以帮助广大研究人员定位目标应用程序中现有和隐藏的文件以及目录。该工具的功能类似于dirb和gobuster,但Urlbuster还提供了大量变异选项。
功能介绍
- 代理支持
- Cookie支持
- 基本身份验证
- 摘要授权
- 重试(对于慢速服务器)
- 持久性和非持久性HTTP连接
- 请求方法:GET、POST、PUT、DELETE、PATCH、HEAD、OPTIONS
- 自定义HTTP头
- 修改POST,PUT和PATCHPayload
- 使用不同的请求方法进行变异
- 使用不同的HTTP头进行变异
- 使用不同的文件扩展名进行变异
- 使用斜杠进行变异
- 枚举GET参数值
工具安装
广大研究人员在配置好Python和pip环境之后,可以直接使用下列命令安装Urlbuster:
pip install urlbuster
工具使用
usage: urlbuster [options] -w <str>/-W <file> BASE_URL urlbuster -V, --help urlbuster -h, --version URL bruteforcer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but also allows to iterate over multiple HTTP request methods, multiple useragents and multiple host header values. positional arguments: BASE_URL The base URL to scan. required arguments: -w str, --word str Word to use. -W f, --wordlist f Path to wordlist to use. optional global arguments: -n, --new Use a new connection for every request. If not specified persistent http connection will be used for all requests. Note, using a new connection will decrease performance, but ensure to have a clean state on every request. A persistent connection on the other hand will use any additional cookie values it has received from a previous request. -f, --follow Follow redirects. -k, --insecure Do not verify TLS certificates. -v, --verbose Show also missed URLs. --code str [str ...] HTTP status code to treat as success. You can use a '.' (dot) as a wildcard. Default: 2.. 3.. 403 407 411 426 429 500 505 511 --payload p [p ...] POST, PUT and PATCH payloads for all requests. Note, multiple values are allowed for multiple payloads. Note, if duplicates are specified, the last one will overwrite. See --mpayload for mutations. Format: <key>=<val> [<key>=<val>] --header h [h ...] Custom http header string to add to all requests. Note, multiple values are allowed for multiple headers. Note, if duplicates are specified, the last one will overwrite. See --mheaders for mutations. Format: <key>:<val> [<key>:<val>] --cookie c [c ...] Cookie string to add to all requests. Format: <key>=<val> [<key>=<val>] --proxy str Use a proxy for all requests. Format: http://<host>:<port> Format: http://<user>:<pass>@<host>:<port> Format: https://<host>:<port> Format: https://<user>:<pass>@<host>:<port> Format: socks5://<host>:<port> Format: socks5://<user>:<pass>@<host>:<port> --auth-basic str Use basic authentication for all requests. Format: <user>:<pass> --auth-digest str Use digest authentication for all requests. Format: <user>:<pass> --timeout sec Connection timeout in seconds for each request. Default: 5.0 --retry num Connection retries per request. Default: 3 --delay sec Delay between requests to not flood the server. --output file Output file to write results to. optional mutating arguments: The following arguments will increase the total number of requests to be made by applying various mutations and testing each mutation on a separate request. --method m [m ...] List of HTTP methods to test each request against. Note, each supplied method will double the number of requests. Supported methods: GET POST PUT DELETE PATCH HEAD OPTIONS Default: GET --mpayload p [p ...] POST, PUT and PATCH payloads to mutate all requests.. Note, multiple values are allowed for multiple payloads. Format: <key>=<val> [<key>=<val>] --mheader h [h ...] Custom http header string to add to mutate all requests. Note, multiple values are allowed for multiple headers. Format: <key>:<val> [<key>:<val>] --ext ext [ext ...] List of file extensions to to add to words for testing. Note, each supplied extension will double the number of requests. Format: .zip [.pem] --slash str Append or omit a trailing slash to URLs to test. Note, a slash will be added after the extensions if they are specified as well. Note, using 'both' will double the number of requests. Options: both, yes, no Default: no misc arguments: -h, --help Show this help message and exit -V, --version Show version information examples urlbuster -W /path/to/words http://example.com/ urlbuster -W /path/to/words http://example.com:8000/ urlbuster -k -W /path/to/words https://example.com:10000/
变异样例
对于某些网站来说,在使用某些特殊用户代理的情况下,即使调用的是相同的路径,Web应用程序的反应和行为也会不同。
$ urlbuster \ -W /usr/share/dirb/wordlists/common.txt \ --mheader 'User-Agent:Googlebot/2.1 (+http://www.googlebot.com/bot.html)' \ --method 'POST,GET,DELETE,PUT,PATCH' \ http://www.domain.tld/
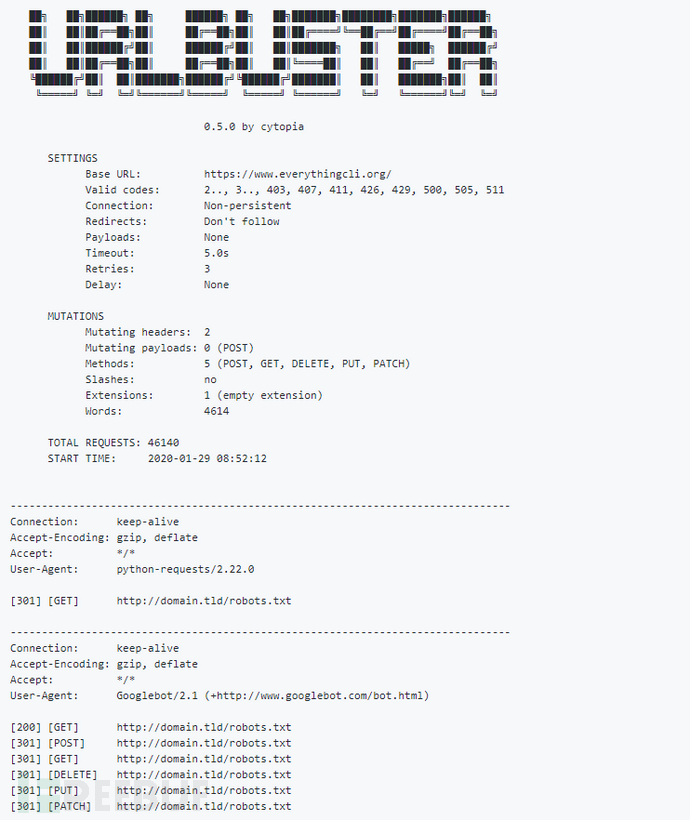
工具使用样例
默认使用方式
基本:
$ urlbuster \ -W /path/to/wordlist.txt \ http://www.domain.tld/
Burpsuite代理:
$ urlbuster \ -W /path/to/wordlist.txt \ --proxy 'http://localhost:8080' \ http://www.domain.tld/
将结果存储至文件:
$ urlbuster \ -W /path/to/wordlist.txt \ --output out.txt \ http://www.domain.tld/
基础认证扫描:
$ urlbuster \ -W /path/to/wordlist.txt \ --auth-basic 'user:pass' \ http://www.domain.tld/
使用会话Cookie:
$ urlbuster \ -W /path/to/wordlist.txt \ --cookie 'PHPSESSID=a79b00e7-035a-2bb4-352a-439d855feabf' \ http://www.domain.tld/
查找文件
查找站点根目录中的文件:
$ urlbuster \ -W /path/to/wordlist.txt \ --code 200 301 302 \ --ext .zip .tar .tar.gz .gz .rar \ http://www.domain.tld/
查找站点子目录中的文件:
$ urlbuster \ -W /path/to/wordlist.txt \ --code 200 301 302 \ --ext .zip .tar .tar.gz .gz .rar \ http://www.domain.tld/wp-content/
高级使用
爆破查询参数:
$ urlbuster \ -W /path/to/wordlist.txt \ --method GET \ --code 200 301 302 \ http://www.domain.tld/search?q=
爆破POST请求:
$ urlbuster \ -W /path/to/wordlist.txt \ --code 200 301 302 \ --method POST \ --payload \ 'user=somename' \ 'pass=somepass' \ 'mail=some@mail.tld' \ 'submit=yes' \ http://www.domain.tld/
爆破变异POST请求:
$ urlbuster \ -w index.php \ --code 200 301 302 \ --method POST \ --mpayload \ 'user=somename1' \ 'user=somename2' \ 'user=somename3' \ 'pass=somepass1' \ 'pass=somepass2' \ 'pass=somepass3' \ 'mail=some@mail1.tld' \ 'mail=some@mail2.tld' \ 'mail=some@mail3.tld' \ 'submit=yes' \ http://www.domain.tld/wp-admin/
用户代理SQL注入:
$ urlbuster \ -W /path/to/wordlist.txt \ --code 5.. \ --method GET POST \ --mheader \ "User-Agent: ;" \ "User-Agent: ' or \"" \ "User-Agent: -- or #" \ "User-Agent: ' OR '1" \ "User-Agent: ' OR 1 -- -" \ "User-Agent: \" OR 1 = 1 -- -" \ "User-Agent: '='" \ "User-Agent: 'LIKE'" \ "User-Agent: '=0--+" \ "User-Agent: OR 1=1" \ "User-Agent: ' OR 'x'='x" \ "User-Agent: ' AND id IS NULL; --" \ http://www.domain.tld/
查找潜在的vhost:
$ urlbuster \ -w / \ --method GET POST \ --mheader \ "Host: internal1.lan" \ "Host: internal2.lan" \ "Host: internal3.lan" \ "Host: internal4.lan" \ "Host: internal5.lan" \ "Host: internal6.lan" \ http://10.0.0.1
许可证协议
本项目的开发与发布遵循MIT开源许可证协议。
项目地址
Urlbuster:【GitHub传送门】
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐





