如何使用Threatest测试端到端威胁检测规则的有效性

关于Threatest
Threatest是一个基于Go开发的安全测试框架,该框架可以帮助广大研究人员测试端到端威胁检测规则的有效性与可用性。
Threatest允许我们使用各种渗透测试技术对目标进行安全检测,并以此验证是否能够触发期望的安全警报。
检测工程
从广义上讲,检测工程是识别与组织相关的威胁、深入了解它们并提出可靠的策略来检测它们的学科。尽管没有标准化流程,但检测工程通常遵循几个阶段:
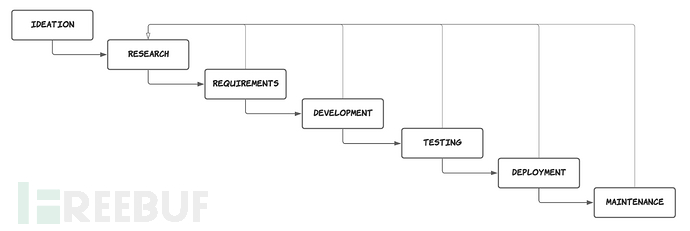
构思:哪些攻击技术与我们的组织相关?
研究:攻击技术是如何工作的?它生成什么日志或遥测数据?
收集要求:实现检测需要哪些日志?我们是否需要更多的可见性或更广泛的范围来实施检测?
开发:定义具体的检测策略以制定检测规则。
测试和部署:测试规则,最好是针对真实世界的数据,以确保它按预期工作,不会产生太多误报。
维护:持续收集检测规则生成的警报指标,并根据需要采取修改和维护。
支持的渗透测试技术和警报匹配器
1、本地命令执行
2、SSH命令执行
3、Stratus红队相关
4、AWS相关
5、Datadog Security信号警报匹配器
工具下载
由于该工具基于Go开发,因此我们首先需要在本地设备上安装并配置好Golang环境。接下来,广大研究人员可以使用下列命令将该项目源码克隆至本地:
git clone https://github.com/DataDog/threatest.git
工具使用
测试Cloud SIEM规则
go test -timeout 99999s cloudsiem_alerts_test.go -v
输出样例:
=== RUN TestCloudSIEMAWSAlerts Detonating 'aws.initial-access.console-login-without-mfa' with Stratus Red Team 2022/06/16 16:31:08 AWS console login: Confirmed that the expected signal (Datadog security signal 'An IAM user was created') was created in Datadog (took 17 seconds). 2022/06/16 16:31:08 AWS console login: Confirmed that the expected signal (Datadog security signal 'AWS Console login without MFA') was created in Datadog (took 17 seconds). 2022/06/16 16:31:08 AWS console login: All assertions passed Detonating 'aws.persistence.iam-create-admin-user' with Stratus Red Team 2022/06/16 16:31:14 AWS persistence IAM user: Confirmed that the expected signal (Datadog security signal 'An IAM user was created') was created in Datadog (took 0 seconds). 2022/06/16 16:31:14 AWS persistence IAM user: All assertions passed --- PASS: TestCloudSIEMAWSAlerts (126.53s) PASS
测试CWS规则
go test cws_alerts_test.go -v
输出样例:
=== RUN TestCWSAlerts Connecting over SSH Connection succeeded 2022/06/16 16:25:20 curl to metadata service: Confirmed that the expected signal (Datadog security signal 'EC2 Instance Metadata Service Accessed via Network Utility') was created in Datadog (took 12 seconds). 2022/06/16 16:25:20 curl to metadata service: All assertions passed 2022/06/16 16:25:42 Java spawning shell: Confirmed that the expected signal (Datadog security signal 'Java process spawned shell/utility') was created in Datadog (took 19 seconds). 2022/06/16 16:25:42 Java spawning shell: All assertions passed --- PASS: TestCWSAlerts (45.64s)
=== RUN TestCWSAlertsV2 Connecting over SSH Connection succeeded === RUN TestCWSAlertsV2/curl_to_metadata_service === PAUSE TestCWSAlertsV2/curl_to_metadata_service === RUN TestCWSAlertsV2/java_spawns_shell === PAUSE TestCWSAlertsV2/java_spawns_shell === CONT TestCWSAlertsV2/java_spawns_shell === CONT TestCWSAlertsV2/curl_to_metadata_service 2022/06/16 16:26:02 curl to metadata service: Confirmed that the expected signal (Datadog security signal 'EC2 Instance Metadata Service Accessed via Network Utility') was created in Datadog (took 11 seconds). 2022/06/16 16:26:02 curl to metadata service: All assertions passed 2022/06/16 16:26:02 java spawns shell: Confirmed that the expected signal (Datadog security signal 'Java process spawned shell/utility') was created in Datadog (took 17 seconds). 2022/06/16 16:26:02 java spawns shell: All assertions passed --- PASS: TestCWSAlertsV2 (0.06s) --- PASS: TestCWSAlertsV2/java_spawns_shell (20.12s) --- PASS: TestCWSAlertsV2/curl_to_metadata_service (20.24s) PASS
测试Stratus Red团队触发的Datadog Cloud SIEM信号
threatest := Threatest()
threatest.Scenario("AWS console login").
WhenDetonating(StratusRedTeamTechnique("aws.initial-access.console-login-without-mfa")).
Expect(DatadogSecuritySignal("AWS Console login without MFA").WithSeverity("medium")).
WithTimeout(15 * time.Minute)
assert.NoError(t, threatest.Run())测试通过SSH运行命令触发的Datadog Cloud Workload Security信号
ssh, _ := NewSSHCommandExecutor("test-box", "", "")
threatest := Threatest()
threatest.Scenario("curl to metadata service").
WhenDetonating(NewCommandDetonator(ssh, "curl http://169.254.169.254 --connect-timeout 1")).
Expect(DatadogSecuritySignal("EC2 Instance Metadata Service Accessed via Network Utility"))
assert.NoError(t, threatest.Run())许可证协议
本项目的开发与发布遵循Apache-2.0开源许可证协议。
项目地址
Threatest:【GitHub传送门】
参考资料
https://securitylabs.datadoghq.com/articles/threatest-end-to-end-testing-threat-detection/
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录





